Facebook users are being targeted by an e-commerce fraud network that uses hundreds of fake websites to steal personal and financial data using brand impersonation and malicious advertising tricks.
Recorded Future’s Payment Fraud Intelligence team, which discovered the company on April 17, 2024, named it ERIAKOS due to its use of the same content delivery network (CDN) as oss.eriakos(.)com.
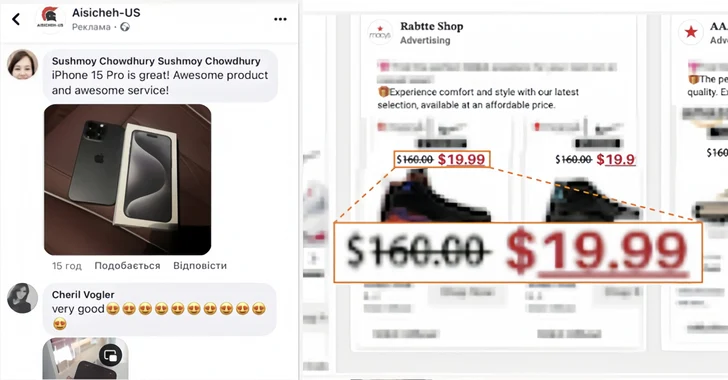
“These fraudulent sites were only accessible via mobile devices and advertising baits, a tactic designed to evade automated detection systems,” the company said in a statement. saidnoting that the network included 608 fraudulent websites and that the activity spanned several short-lived waves.
A notable aspect of the sophisticated campaign is that it was exclusively targeted at mobile users, who visited the scammers’ sites via Facebook ad baits, some of which relied on limited-time discounts to entice users to click on them. Recorded Future said up to 100 meta-ads linked to a single scam site are served per day.

The fake websites and ads were found to mainly impersonate a major online e-commerce platform and power tool manufacturer, and targeted victims with fake offers to sell products from various well-known brands. Another important distribution mechanism involves the use of fake user comments on Facebook to lure potential victims.
“Merchant accounts and related domains associated with fraudulent websites are registered in China, indicating that the threat actors operating this campaign may have established a business that they use to manage fraudulent accounts merchants in China,” Recorded Future noted.
This is not the first time criminal e-commerce networks appeared with the aim of collecting credit card information and making an illegal profit from fake orders. In May 2024, a huge network of 75,000 fake online stores – the so-called BogusBazar – was found to have earned more than $50 million from advertising name-brand shoes and clothing at low prices.
Then, last month, Orange Cyberdefense discovered a previously undocumented traffic routing system (TDS) under the name R0bl0ch0n TDS used to promote affiliate marketing scams through a network of fake stores and tote sites for the purpose of obtaining credit card information.
“Several separate vectors are used to initially distribute the redirect URLs via R0bl0ch0n TDS, indicating that these campaigns are likely run by different affiliates,” said security researcher Simon Verneen said.
The development comes in the wake of fake Google ads being displayed when searching for Google Authenticator on the search engine is observed redirecting users to a fake site (“chromeweb-authenticators(.)com”) that delivers a Windows executable hosted on GitHub that eventually removes the information stealer called DeerStealer.
What makes the ads seem legitimate is that they appear to come from “google.com” and that the advertiser’s identity has been verified by Google, according to Malwarebytes, which says that “some unknown person was able to issue pretend to be Google and successfully push malicious software disguised as a Google branded product.”
Malware campaigns have also been spotted distributing different malware families, e.g SocGholish (aka FakeUpdates), MadMxShelland WorkersDevBackdoorwith Malwarebytes detecting infrastructure overlaps between the latter two, indicating that they are likely run by the same threats.
In addition, advertisements for Angry IP Scanner were used to lure users to fake websites, and the email address “goodgoo1ge@protonmail(.)com” was used to register domains that deliver MadMxShell and WorkersDevBackdoor.
“Both malware payloads have the ability to collect and steal sensitive data, as well as provide direct access to the initial access brokers involved in the deployment of ransomware,” security researcher Jerome Segura said.