Cybersecurity researchers are warning of a new phishing campaign targeting Microsoft OneDrive users to execute a malicious PowerShell script.
“This company relies heavily on social engineering tactics to get users to execute a PowerShell script, thereby compromising their systems,” Rafael Pena, Trellix security researcher. said in Monday’s analysis.
A cyber security company is tracking a “cunning” phishing and download campaign called OneDrive Pastejacking.
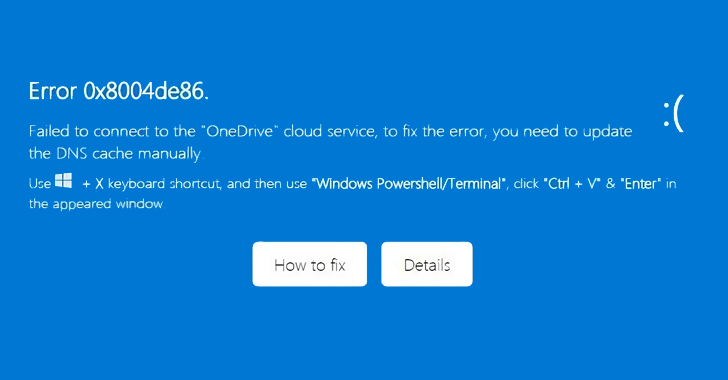
The attack is deployed via an email that contains an HTML file that, when opened, displays an image that mimics the OneDrive page and displays an error message that reads: “Failed to connect to the OneDrive cloud service.” To fix the error, you need to refresh the DNS cache manually.”
The message also contains two options, namely “How to fix” and “Details”, the latter of which directs the email recipient to a legitimate Microsoft Learn DNS troubleshooting page.
However, clicking “How to fix” prompts the user to follow a series of steps that include pressing Windows Key + X to open a shortcut menu, launching a PowerShell terminal, and inserting a Base64-encoded command to supposedly fix the error. question.

“The (…) command first runs ipconfig /flushdns, then creates a folder on the C: drive called ‘downloads,'” Pena explained. “It then downloads the archive file to that location, renames it, extracts its contents (‘script.a3x’ and ‘AutoIt3.exe’) and executes script.a3x with AutoIt3.exe.”
The campaign targeted users in the US, South Korea, Germany, India, Ireland, Italy, Norway and the UK
The disclosure is based on similar findings from ReliaQuest, Proofpointand McAfee Laboratoriesindicating that phishing attacks using this technique – also tracked as ClickFix – are becoming more common.
The development comes amid the unveiling of a new email-based social engineering campaign distribution forged Windows shortcut files that lead to the execution of malicious payloads hosted on Discord’s Content Delivery Network (CDN) infrastructure.
Phishing campaigns are also on the rise, such as sending Microsoft Office Forms from previously compromised legitimate email accounts to trick subjects into revealing their Microsoft 365 login credentials by clicking on a seemingly innocuous link.
“Attackers create legitimate forms in Microsoft Office Forms by embedding malicious links into the forms,” - Perception Point said. “These forms are then mass emailed to targets under the guise of legitimate requests, such as changing passwords or accessing important documents, impersonating trusted platforms and brands such as Adobe or Microsoft’s SharePoint document viewer.”
Moreover, there are other waves of attacks used invoice-themed lures to trick victims into sharing their credentials on phishing pages hosted on Cloudflare R2 which are then transmitted to the threat actor via the Telegram bot.
It is not surprising that opponents are constantly on the lookout in different ways to sneak malware past Secure Email Gateways (SEGs) to increase the likelihood of their attacks succeeding.
According to a recent Cofense report, bad actors are abusing the way SEGs scan ZIP archive attachments to deliver Form information stealer using DBatLoader (aka ModiLoader and NatsoLoader).
Specifically, this involves passing the HTML payload as an MPEG file to avoid detection, taking advantage of the fact that many common archive extractors and SEGs parse the file’s header information, but ignore the file’s footer, which may contain more precise format information. file.
“The threat actors used a .ZIP archive attachment, and when SEG scanned the contents of the file, it was found that the archive contained an .MPEG video file and had not been blocked or filtered,” the company said in a statement. noted.
“When this attachment was opened with common/popular archive extraction tools like 7-Zip or Power ISO, it appeared to also contain an .MPEG video file, but it did not play. However, when the archive was opened in the Outlook client or through Windows Explorer’s archive manager, the .MPEG file is (correctly) identified as a .HTML (file).”