A recently patched security flaw affecting VMware ESXi hypervisors has been actively exploited by “several” ransomware groups to gain elevated permissions and deploy file-encrypting malware.
Attacks involve exploitation CVE-2024-37085 (CVSS Score: 6.8), an Active Directory integration authentication bypass that allows an attacker to gain administrative access to a host.
“An attacker with sufficient Active Directory (AD) permissions can gain full access to an ESXi host that was previously configured to use AD for user management by re-creating the configured AD group (“ESXi Administrators” by default) after deleting it. from AD, VMware owned by Broadcom noted in a recommendation published at the end of June 2024.
In other words, escalating privileges on ESXi for an administrator was as simple as creating a new AD group called “ESX Administrators” and adding any user to it, or renaming any group in the domain to “ESX Administrators” and adding the user to the groups or using of an existing group member.
Microsoft, in a new analysis published on July 29, said it had observed such ransomware operators Storm-0506Storm-1175, October storm and manatee storm using a post-compromise technique to deploy Akira and Black Basta.

“VMware ESXi hypervisors joined to an Active Directory domain by default consider any member of the domain group named ‘ESX Administrators’ to have full administrative access,” – Researchers Daniel Kuznets Nokhi, Edan Zwick, Meitor Pinto, Charles-Edouard Betton, and Vaibhav Deshmukh said.
“This group is not a built-in group in Active Directory and does not exist by default. ESXi hypervisors do not check that such a group exists when the server is joined to a domain, and still consider members of a group with that name to have full administrative access, even if the group did not initially exist.”
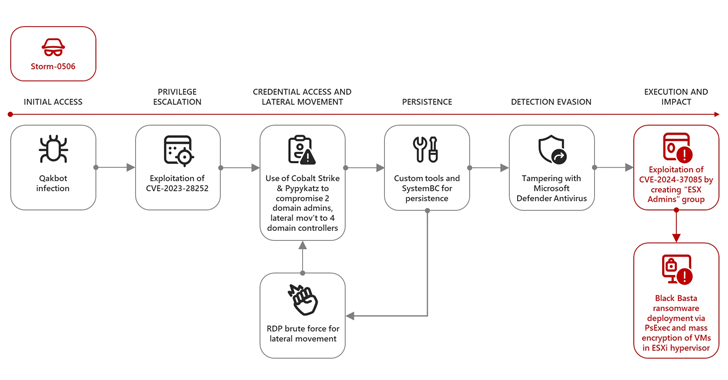
In one attack by Storm-0506 against an unnamed engineering firm in North America, a threat actor exploited the vulnerability to gain elevated access rights to ESXi hypervisors after gaining initial foothold with QakBot infecting and exploiting another flaw in the Windows Common Log File System (CLFS) driver (CVE-2023-28252CVSS score: 7.8) to increase privileges.
Subsequent stages entailed the deployment of Cobalt Strike and PipykatsPython Version of Mimikatz to Steal Domain Admin Credentials and Traverse the Network Then Remove SystemBC implant for persisting and abusing ESXi admin access to deploy Black Basta.
“The actor also attempted to connect Remote Desktop Protocol (RDP) to multiple devices as another method of lateral movement and then reinstalled Cobalt Strike and SystemBC,” the researchers said. “The threat actor then attempted to spoof Microsoft Defender Antivirus using various tools to avoid detection.”
The development comes after Google-owned Mandiant discovered a cluster of financially motivated threats calling UNC4393 uses the original access gained through a backdoor codenamed C/C++ ZLoader (aka DELloader, Terdot, or Silent Night) to deliver Black Basta while moving away from QakBot and DarkGate.
“UNC4393 has demonstrated a willingness to work with multiple distribution clusters to execute its actions on targets,” the threat intelligence firm reported said. “The most recent surge in Silent Night activity, which began earlier this year, was largely driven by malicious advertising. This marked a marked departure from phishing as the only known method of initial access to UNC4393.”
The attack sequence includes using initial access to reset the Cobalt Strike Beacon and a combination of custom and off-the-shelf tools to conduct reconnaissance, not to mention using RDP and Server Message Block (SMB) for lateral traffic. Persistence is achieved using SystemBC.
ZLoader which surfaced again after a long hiatus late last year, is in active development with new variants of malware spread through a PowerShell backdoor called PowerDashtrans recent findings from Walmart’s cyber intelligence team.
Over the past few years, ransomware actors have increasingly demonstrated a willingness to embrace new techniques to maximize exposure and evade detection focused on ESXi hypervisors and using newly discovered security flaws on servers with internet access to hack interesting targets.
Do it (aka Agenda), for example, was originally developed in the Go programming language but has since been refactored using Rust, indicating a shift toward creating malware using memory-safe languages. Recent ransomware attacks have been found to exploit known vulnerabilities in Fortinet and Veeam Backup & Replication software to gain initial access.
“Qilin ransomware is capable of self-propagating over a local network,” Group-IB said in a recent analysis, adding that it is also equipped to “perform self-provisioning with VMware vCenter.”
Another known malware used in Qilin ransomware attacks is a tool called Ultra killer designed to disable popular Endpoint Detection and Response (EDR) software running on an infected host, and clean all Windows event logs to remove all indicators of a breach.
Organizations are encouraged to install the latest software updates, practice credential hygiene, implement two-factor authentication, and take steps to protect critical assets with appropriate monitoring procedures and backup and recovery plans.