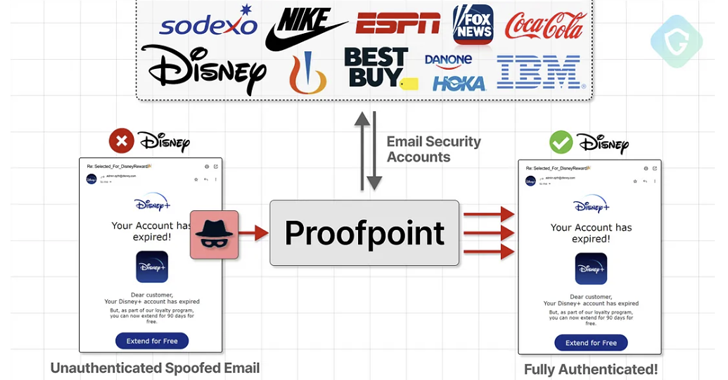
An unknown threat actor has been linked to a massive fraud campaign that used email routing misconfigurations in email security vendor Proofpoint’s defenses to send millions of messages impersonating various popular companies such as Best Buy, IBM, Nike, and Walt Disney, among others. others.
“These emails originated from official Proofpoint authenticated email relays SPF and DKIM signaturesthus bypassing basic security measures – all in order to trick recipients and steal funds and credit card data.” – Guardio Labs researcher Nati Tal said in a detailed report shared with The Hacker News.
A cyber security company named the company EchoSpoofing. The activity is believed to have begun in January 2024, and the threat actor used the vulnerability to send an average of three million emails per day, peaking at 14 million in early June, when Proofpoint began taking countermeasures.
“The most unique and powerful part of this domain is the spoofing method, which leaves almost no chance to understand that it is a fake email sent by these companies,” Tal told the publication.
“This concept of EchoSpoofing is really powerful. It’s strange that it’s used for large-scale phishing like this, instead of a boutique phishing campaign, where an attacker can quickly get the identity of any real member of the company’s team and send emails to other employees – ultimately, through high-level social engineering, to gain access to internal data or credentials and even compromise the entire company.
The technique, which involves threat actors sending messages from an SMTP server to a virtual private server (VPS), is notable for its compliance with authentication and security measures such as SPF and DKIM, which stand for Sender Policy Framework and DomainKeys Identified Mail, respectively, and refer to authentication methods that are designed to prevent attackers from impersonating a legitimate domain.

It boils down to the fact that these messages are routed from various Microsoft 365 tenants controlled by the adversary, which are then relayed through the email infrastructures of Proofpoint’s corporate clients to reach users of free email providers such as Yahoo!, Gmail, and GMX.
This is the result of what Guardio described as a “super-permissive misconfiguration flaw” in Proofpoint’s (“pphosted.com”) servers, which essentially allowed spammers to take advantage of the email infrastructure to send messages.
“The root cause is a modified email routing configuration feature on Proofpoint’s servers that allows outbound organization messages to be relayed from Microsoft 365 tenants, but without specifying which M365 tenants to allow,” – Proofpoint said in a coordinated disclosure report shared with The Hacker News.
“Any e-mail infrastructure that offers this e-mail routing configuration feature can be abused by spammers.”
In other words, an attacker could use the flaw to set up fake Microsoft 365 tenants and deliver spoofed emails to Proofpoint’s relay servers, where they are “delivered” as genuine digital messages impersonating customer domains.
This, in turn, is accomplished by configuring the Exchange server’s outgoing email connector directly to the vulnerable pphosted.com endpoint associated with the client. Also, a hacked version of a legitimate email delivery software called PowerMTA used to send messages.
“The spammer used a recurring series of virtual private servers (VPS) leased from multiple vendors, using many different IP addresses, to initiate rapid bursts of thousands of messages simultaneously from their SMTP servers, which are sent to Microsoft 365 for transmission to Proofpoint-hosted customer servers.” Proofpoint said.
“Microsoft 365 was receiving these spoofed messages and sending them to these customers’ email infrastructures for relaying. When customer domains were spoofed while relaying through the respective customer’s email infrastructure, the DKIM signature was also applied when messages passed through Proofpoint’s infrastructure, making spam messages more accessible.”
It is suspected that EchoSpoofing was deliberately chosen by the operators as a way to generate illegal income, and also as a way to avoid the risk of disclosure for long periods of time, as directly targeting companies with this modus operandi could dramatically increase the chances of being detected, effectively endangering the whole scheme.
At the same time, it is still unclear who is behind the company. Proofpoint said the activity does not intersect with any known threat or group.
“In March, Proofpoint researchers identified spam campaigns being transmitted through a small amount of Proofpoint customers’ email infrastructure, sending spam from Microsoft 365 tenants,” the statement said. “All analysis indicates that this activity was carried out by a single spam actor, whose activities we do not attribute to a known organization.”
“Since the discovery of this spam campaign, we have worked diligently to provide remedial guidance, including implementing an optimized administrative interface for customers to determine which M365 tenants are allowed to relay and all other M365 tenants are denied by default.”
Proofpoint stressed that no customer data was exposed and none experienced data loss as a result of these campaigns. He also noted that he contacted some of his customers directly to request that they change their settings to stop the outbound spam relay from being effective.
“As we began blocking the spammer’s activity, the spammer accelerated testing and quickly moved on to other customers,” the company said. “We have established a continuous process to identify affected customers every day, prioritizing coverage to fix configurations.”
To reduce spam, he urges VPS providers to limit their users’ ability to send large volumes of messages from SMTP servers hosted on their infrastructure. It also urges email service providers to restrict free trial options and newly created unverified tenants to bulk outbound email messages, and to prevent them from sending messages that impersonate a domain they have not verified ownership of.
“For CISOs, the key takeaway here is to pay close attention to your organization’s cloud posture, particularly with the use of third-party services that become the foundation of your company’s networking and communications practices,” Tal said. “Especially when it comes to email, always maintain feedback and self-monitoring – even if you completely trust your email provider.”
“As for other backbone companies like Proofpoint, they need to be vigilant and proactively address all possible types of threats. Not just threats that directly affect their customers, but the general public as well. good.
“This is critical to the security of us all, and the companies that build and operate the Internet’s core network, even if they are privately owned, bear the biggest responsibility. As has been said, in a completely different context, but very relevant here: “With great power comes great responsibility.”