Details have emerged of a “massive ad fraud operation” using hundreds of apps on the Google Play Store to carry out a host of nefarious activities.
The company received a code name Confetti – the Russian word for Candy – due to abuse of a mobile advertising software kit (SDK) linked to a Russian ad network called CaramelAds.
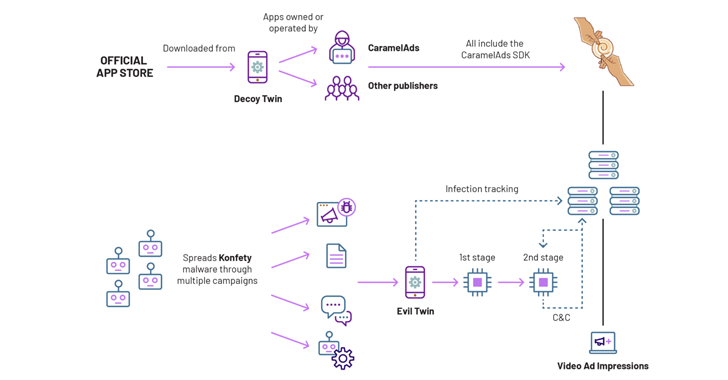
“Konfety represents a new form of fraud and obfuscation in which threat actors operate ‘evil twin’ versions of decoy programs available in major markets,” Satori Threat Intelligence Team HUMAN said in a technical the report shared with The Hacker News.
While the more than 250 rogue apps are harmless and distributed through the Google Play Store, their respective “evil twins” are distributed through a malicious ad campaign designed to promote ad fraud, monitor web searches, install browser extensions and sideloading APK files encode on users’ devices.
The most unusual aspect of the campaign is that the evil twin masquerades as a decoy twin by spoofing the latter’s app ID and ad publisher IDs to render ads. Both rogue and malicious application twin sets run on the same infrastructure, allowing threat actors to exponentially scale their operations as needed.

However, the cheat apps not only behave normally, most of them don’t even display ads. They also include a GDPR consent notice.
“This decoy/evil double obfuscation mechanism is a novel way for threat actors to present fraudulent traffic as legitimate,” the HUMAN researchers said. “At its peak, the programmatic volume associated with Konfety reached 10 billion requests per day.”
In other words, Konfety uses the ad rendering capabilities of the SDK to commit ad fraud, making it much harder to distinguish between malicious and legitimate traffic.
The evil Konfety twin apps are said to be distributed through a malicious ad campaign that promotes APK mods and other software such as Letasoft Sound Booster with mined URLs hosted on attacker-controlled domains, hacked WordPress sites, and other platforms. that allow you to upload content, including Docker Hub, Facebook, Google Sites, and OpenSea.
Users who end up clicking on these URLs are redirected to a domain that tricks them into downloading a malicious twin app, which in turn acts as a dropper for the first stage, which is decrypted from the APK file’s assets and used to configure command-administrative (C2) communication.
The initial stage further attempts to hide the app icon from the device’s home screen and launches a second-stage DEX payload that performs the trick by showing an out-of-context full-screen video ad while the user is on the home screen or using another app.
“The core of Operation Konfety is evil twin programs,” the researchers said. “These apps impersonate their respective decoy twin apps by copying their app IDs/package names and publisher IDs from the decoy twin apps.”
“Network traffic originating from Evil twin applications is functionally identical to network traffic originating from decoy twin applications; ad impressions served by evil twins use the name of the twin decoy package in the request.”
Other capabilities of the malware include weaponizing the CaramelAds SDK to visit websites using the default web browser, tricking users by sending them notifications that prompt them to click on fake links, or sideloading modified versions of other ad SDKs.
That’s not all. Users who install Evil Twins apps are encouraged to add a search toolbar widget to their device’s home screen that secretly monitors their searches by sending data to domains named vptrackme(.)com and youaresearching(.)com.
“Threat actors understand that placing malware in stores is not a stable technique and are finding creative and clever ways to avoid detection and commit long-term fraud,” the researchers concluded. “Actors creating SDK middlemen and distributing SDKs to abuse high-end publishers are a growing technique.”