The threat actor, which was previously observed using an open-source network mapping tool, has expanded its operations significantly, infecting more than 1,500 victims.
Sysdig monitoring the cluster named CRYSTALsaid activity has seen a 10-fold spike, adding that it includes “mass scanning, exploiting multiple vulnerabilities and deploying backdoors using multiple security tools (open source software).”
The main purpose of the attacks is to collect and sell credentials, deploy cryptocurrency miners, and maintain stability in the victim’s environment.
Among the open source programs used by the threat actor, it occupies a large place SSH-Snakewhich was first released in January 2024. It was described as a tool for automatic network traversal using private SSH keys discovered on systems.
CRYSTALRAY abused the software documented by the cybersecurity company earlier this February with the tool deployed for lateral movement after exploiting known security flaws in public instances of Apache ActiveMQ and Atlassian Confluence.
Joshua Rogers, the developer of SSH-Snake, told The Hacker News at the time that the tool only automates what would otherwise be a manual step, and urged companies to “discover the attack paths that exist and fix them.”
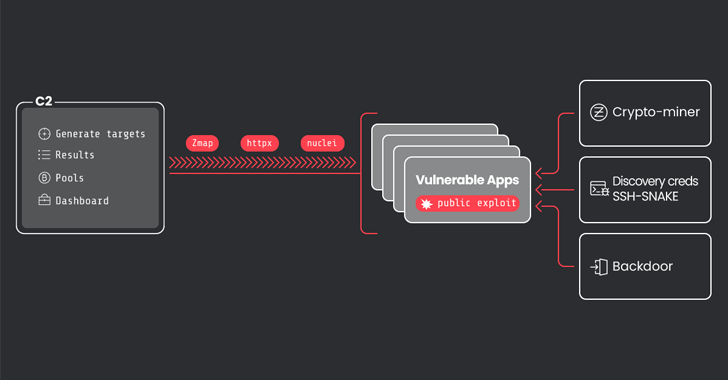
Some of the other tools used by attackers include base, map, httpxand nuclei to check if the domain is active and run a scan for vulnerable services such as Apache ActiveMQ, Apache RocketMQ, Atlassian Confluence, Laravel, Metabase, Openfire, Oracle WebLogic Server, and Solr.

CRYSTALRAY also uses its native database to perform an extensive credential discovery process that goes beyond traversing between servers accessible via SSH. Permanent access to the compromised environment is achieved through a legitimate command and control (C2) system called A scrap and a reverse shell manager under the code name Duckbills.
In a further attempt to extract monetary value from the infected assets, cryptocurrency miner payloads are delivered to illegally exploit the victim’s resources for financial gain, while taking steps to shut down rival miners that may already be running on the machines.
“CRYSTALRAY is capable of discovering and extracting credentials from vulnerable systems that are then sold on black markets for thousands of dollars,” said Sysdig researcher Miguel Hernandez. “Accounts being sold include a variety of services, including cloud service providers and SaaS email providers.”