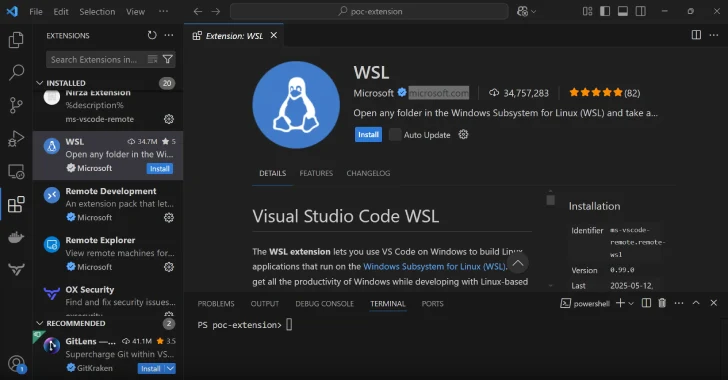
New Integrated Development Environment Study (IDES), such as Microsoft Visual Studio Code, Visual Studio, Intellij Ideea and Cursor, revealed weaknesses in how they handle the expansion process, ultimately allowing the attackers to perform malicious code for developers.
“We found that checking checks in the Visual Studio code allows publishers to add functionality to extensions while maintaining a proven icon,” – Researchers on Ox Nir Zadok and Moshe Siman Tov Bustan – Note In a report that shared with Hacker News. “This leads to the potential for malicious extensions to be checked and approved, creating a false sense of trust.”
In particular, the analysis showed that the Visual Studio code sends a request to the HTTP message to the “MarketPlace.visualstudio (.) Com” to determine the extension or so.
The method of operation is essentially the creation of malicious expansion with the same proven values as the already proven expansion, such as Microsoft, and the treatment of trust check.
As a result, this allows the expansion of the times that look proven for non -suspicious developers, and contain a code capable of performing the operating system commands.
In terms of security, it is a classic case of expansion, where bad actors distribute plugins in the official market. Without proper signing the application code or trusted check out, even legitimate extensions can hide dangerous scenarios.
For attackers, this opens the entry point to the low barrier to achieve the remote codes, which is particularly serious in the development environment where sensitive credentials and the source code are often available.
In the concept check (POC) demonstrated by cybersecurity company, the extension was set up to open the Windows Calculator application, thus emphasizing its ability to perform commands on the main host.
Determining the values used in the verification requests and changing them, it was found that you can create a VSIX package file so that it leads to the malicious extension.
Ox Security said it was capable of playing other IDEs like IDEALIJ IDEA and Cursor, changing the values used to check without forcing them to lose their proven status.
In response to the responsible disclosure of Microsoft’s information, the behavior is to design and that changes will prevent the publication of VSIX expansion from the signing check, which is included by default on all platforms.
However, the cybersecurity campaign revealed a deficiency that will be operated recently on June 29, 2025. Hacker News turned to Microsoft for comments and we will update the story when we hear back.
The resulting data once again shows that relying solely on a proven expansion character, it can be risky as the attackers can deceive developers to run a malicious code without their knowledge. To mitigate such risks, it is recommended to install extensions directly from the official markets as opposed to using VSIX extension files that are shared online.
“The ability to enter a malicious code in expanding, packing them as VSIX/Zip files and installing them while maintaining proven characters on several major development platforms, creates a serious risk,” the researchers said. “This vulnerability particularly affects the developers that install online resources such as GitHub.”