The threatening subjects behind the Qiilin Ransomware Service Scheme (RAAS) now offers a legal lawyer for affiliates to put more pressure on the victims to pay because a group of cybercrime enhances its activity and tries to fill the void left by its rivals.
The new feature has the form of a “lawyer’s lawyer” on the affiliate panel, for Israeli cybersecurity Cyber.
Development represents new revival From the electronic crimes group, as once popular ransom groups such as Lockbit, Black Cat, RansomHub, Everest and Blacklock, harsh cessions, surgical failures and defects have suffered. A group, which is also monitored as a golden feather and galura water, has been active since October 2022.
The data composed of the Dark Internet leaks, which are conducted by Ransomware, indicate that Qilin led 72 victims in April 2025. In May, it is estimated to be behind 55 attacksputting it behind Safepay (72) and Lim Mor (67). This is also the third according to the active group after CL0P and Akira since the beginning of the year, claiming a total 304 victims.
“Qilin stands over the rest with its fast-growing market due to mature ecosystem, extensive support options for customers and reliable solutions to provide highly focused, high exposure to ransom designed to need significant payments,” Qualys – Note In the group’s analysis this week.
There are data that suggest that the branches running on RansomHub have moved to Qilin, contributing to the spike in Qilin Ransomware in recent months.
“With increasing presence on forums and trackers at requirements, Qilin works technically mature infrastructure: useful loads in rust and C, loaders with expanded evasion features, as well as an affiliate panel that offers a safe execution mode, distribution of the network, clearing the magazines and automated talks.” Ananinine Ananine – Note.
“Outside the malicious software, Qilin offers spam services, PB-Major storage, legal recommendations and a complete set of operations-not only as a ransom group, but also as a platform for cybercrime with full service.”
The decline and death of other groups were supplemented by new updates to the Qilin Affiliate College, including a new legal aid function, a team of own journalists and the possibility of conducting widespread attacks (DDOS). Another notable application is the tool for spam corporate email addresses and phone numbers.
The expansion of the function indicates an attempt on the part of the threatening subjects as selling themselves as a full -fledged cybercrime service that goes beyond simple redemption.
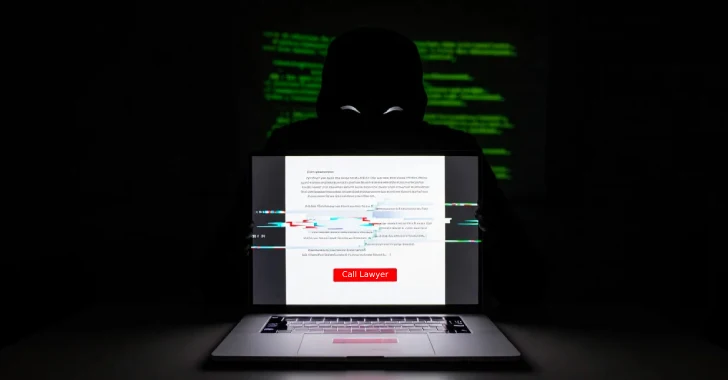
“If you need legal advice on your target, just click the” Call Lawyer “button located in the target interface, and our legal team will contact you privately to provide qualified legal support,” the forum said in the translated version of the forum.
“A simple appearance of a lawyer in the chat can put indirect pressure on the company and increase the amount of redemption because companies want to avoid trial.”
Development comes as property evaluated that at least one branch of rhysida started using Utility with open source call Pyramid eye C2 Probably as a tool after a compromise to maintain access to compromised end points and providing additional useful loads.
It is worth noting that Pyramid eye C2 refers to the same Based on python back This was deployed by the threat -related threat to the RansomHub crew in the 2024 quarter.
It also follows from a new analysis Black log leaks bastaWhat a shedding light on the actor threatened, which went through the online Tinker. Their identity in the real world is currently unknown.
It is said that Tinker, Per Intel 471, is one of the TRAP’s proxies, the group leader, and joined the criminal enterprise as a “creative director” after the previous experience of launched call centers, including for the already non-existent CONTI group, as well as as a negotiating participant for Blacks (AKA ROL).
“Actor Tinker played an important role in providing initial access to organizations,” cybersecurity campaign – Note. “The talked conversations show that Tinker analyzes financial data and evaluates the situation with the victim before direct negotiations.”
The actor threats, in addition to conducting open source research to obtain contact information for the company’s senior staff in order to extort them either through telephone calls or reports, was instructed to write phishing-leaf designed to violate organizations.
Tinker, in particular, also came up with Script Phisching based on Microsoft TeamsAs a result, the attackers are disguised as an IT officer, warning the victims that they are in a spam attack and urge employees to install a remote desktop, such as anydesk, and give them access to allegedly securing their systems.
“After installing the RMM software, the subscriber will contact one of the Black Basta penetration testists, which would then move on to sustainable access to the system and domain,” Intel 471 said.
Subbound messages also indicate that Tinker received at least $ 105,000 for his efforts from December 18, 2023 to June 16, 2024. This is said to be unclear for which group they can work for.
The conclusions are the same exam unnamed 33-year-old foreign member Rick Ransomware Group in the United States for their intended role as a Boker of original access (IAB) and promoting access to corporate networks. The suspect was arrested from Kiev in early this April at the request of the US law enforcement.
A member “Searching for vulnerabilities in corporate networks of the victim enterprises,” National Police of Ukraine – Note In a statement. “The data obtained by the hacker was used by his accomplices to plan and carry out cyberattacks.”
Authorities said they were able to trace the suspect after the trial of the equipment confiscated in the previous raid that occurred in November 2023 Signing on the members of Lockergoga, Megacortex and Dharma Ransomware.
Elsewhere, police officers in Thailand detained several Chinese citizens and other South Asia suspects after a raid at a Pattaya Hotel, which was used as a gambling nativity and as offices for redemption operations.
Six Chinese citizens who sent malicious links to the company to infect them with ransomers are said to be in charge of the ransomware. Reports on local media talk They were the staff of the cybercrime gang, who paid for the distribution of signed bubbies with Chinese firms.
This week is also the Central Bureau of Thailand (CIB) announced The arrest of more than a dozen foreigners under the Firestorm operation for allegedly launching an online battery that cheated on several victims in Australia, calling them and deceiving their money into long-term bonds with a promise of high profitability.