On Thursday, Cloudflare said he was autonomously blocked the largest in the history of the Service of Service (DDOS), which has ever been recorded, which reached the peak of 7.3 teraobes per second (TBPS).
The attack, which was discovered in mid -May 2025, sent an unnamed hosting supplier.
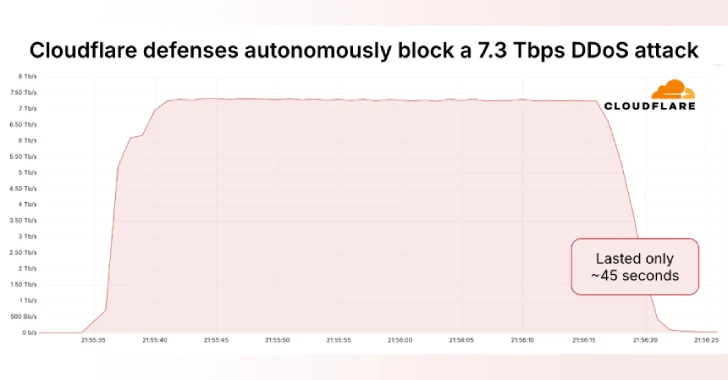
“Hosting providers and critical internet infrastructure are increasingly becoming DDOS attacks,” – Oomer Yoachimik Cloudflare – Note. “Attack 7.3 TBP put 37.4 terabytes in 45 seconds.”
Earlier in January this web -infrastructure and security company – Note He softened the DDOS 5.6 TBPs attack, aimed at an unnamed Internet service provider (provider) from East Asia. In October 2024, the attack emerged from the Mirai-Borans.
Then in April 2025 Cloudflare disclosed He defended himself from massive 6.5 TBP floods, which most likely came out of eleven11 bot, a botten consisting of approximately 30,000 webcams and videos. Hyper-stop-stand lasted about 49 seconds.
Compared to 7.3 TBPS DDOS, compared to the carpet, an average of 21 925 destination desks that owned and used a hosting provider by striking the crest of 34 517 destination desks per second.
The attack with multiple vectors arose from the same spread-pigs and was defined as a combination of UDP flood, QotD attacks, reflex attacks, NTP reflection attacks, attacks on Mirai UDP floods, flooding and ripv1 enhancement. The UDP Flood was 99,996% of the attack.
Cloudflare also noted that the attack occurred with more than 122 145 IP sources covering 5 433 standalone systems (AS) in 161 countries. The main sources of the attack included Brazil, Vietnam, Taiwan, China, Indonesia, Ukraine, Ecuador, Thailand, USA and Saudi Arabia.
“The average number of unique IP -Drasses per second was 26 855 with a peak 45 097,” Joachimik said.
“Telefonica Brazil (AS27699) accounts for the largest part of the DDOS traffic, which is responsible for 10.5%. Viettel Group (AS7552) closely monitors 9.8%, and China Unicom (AS4837) and Chunghwa Telecom (AS3462) Accordingly.
Disclosure occurs as a Qianxin Xlab team – Note DDOS Botnet was tracked when Rapperbot stood behind an attack aimed at artificial intelligence (AI) Depth In February 2025 and the latest samples of malware trying to demand the victims to pay them a “defense fee” to avoid orientation on DDOS attacks in the future.
China, USA, Israel, Mexico, UK, Greece, Iran, Australia, Malaysia and Thailand are the main countries where the devices are infected with rapper. As is known in the botnet Active since 2022.
Rapperbot companies are known to target routers, network storage devices and video recordings with default or firmware vulnerability for initial access, and loss of malicious software that can make contact with a remote server DNS TXT RECORDS To get DDOS Attack Commands.
Malicious software also uses custom encryption algorithms to encrypt TXT and team records (C2) used by domains.
“Since March, his attack has been significantly active, on average more than 100 targets a day and watched more than 50,000 boots,” the Chinese security provider said.
“The targets of the rapper attacks throughout areas of different industries, including public administration, social security and social organizations, online platforms, production, financial services, etc.”