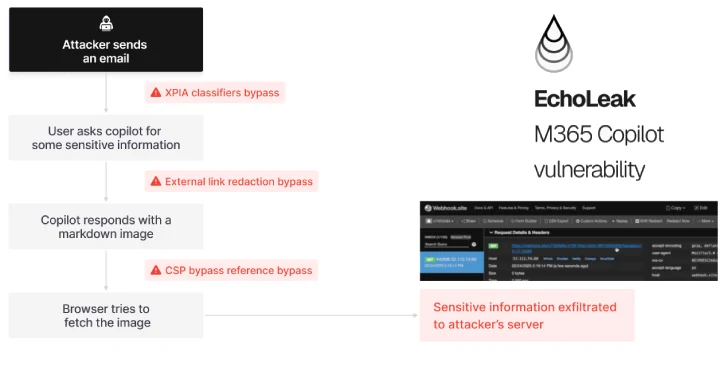
The new attacker called Echoleak has been described as vulnerability of artificial intelligence (AI) with zero click (AI), which allows poor actors to allocate sensitive data from the context of Microsoft 365 Copilot, which provide any interaction of users.
The vulnerability of the critical evaluation was assigned to the CVE-2025-32711 ID (CVSS: 9.3). This does not require customer action and has already addressed Microsoft. There is no evidence that the deficiency was used angrily in the wild.
“The introduction of AI teams in M365 Copilot allows an unauthorized attacker to disclose information on the network,” the company – Note in a consultation released on Wednesday. Since then it has been added to List Microsoft Patch on Tuesday In June 2025, taking the total number of fixed deficiencies to 68.
Security assessment that revealed and reported it, – Note This is an instance of a wide linguistic model (LLM) that conducts a violation that opens the way Indirect operational injectionleading to unintended behavior.
LLM volume violation occurs when the attacker’s instructions laid in unreliable contents, such as an electronic message sent from the organization, successfully deceive the AI system to access and process the privileged domestic data without apparent user intentions and interaction.
“Networks allow the attackers to automatically exploit sensitive and own information from the context of M365 Copilot, without awareness of the user or relying on any specific victim behavior,” said the Israeli cybersecurity campaign. “The result is achieved, despite the fact that the M365 Copilot interface is only open to the organization’s employees.”
The sequence of the attack unfolds as follows –
- Injection: The attacker sends a harmless letter to an employee’s mailbox that includes the operation of LLM Volume
- The user asks at Microsoft 365 Copilot related to business (eg, summarize and analyze the report on their income)
- Disruption of the sphere: Copilot mixes unbearable incoming input with sensitive data into the LLM context for generation (Rag) the engine
- Getting: Copilot leaks sensitive data to the attacker through Microsoft commands and URL SharePoint
“Like AI vulnerability with zero click, Echoleak opens up great opportunities for data exports and extortion for motivated threat subjects,” said AIM Security. “In a permanent world, it demonstrates the potential risks inherent in the development of agents and chats.”
“The attack leads to allow the attacker to highlight the most sensitive data from the current LLM-and LLM context is used against themselves to make sure that the most sensitive data from the LLM context is traced, does not rely on specific behavior of users, and can be performed both in conversations with one-off conversations.”
MCP and advanced tool poisoning
Disclosure occurs when Cyberark revealed an attack by the tools (TPA) It affects the context model protocol (Mcp) Standard and goes beyond the instrument description to expand it throughout the tool scheme. The attack technique was called a complete scheme (FSP) poisoning.
“While much of attention around the attacks of the tools was focused on the field of description, it significantly underestimates another potential surface of the attack,” Simcha Cosman’s security researcher – Note. “Each part of the tool scheme is a potential point of the injection, not just a description.”
Cybersecurity company said the problem is implemented in a “fundamentally optimistic trust model” MCP, which equates syntactic semantic security and suggests that LLMS is only a clear documentary behavior.
Moreover, TPA and FSP may be armed with advanced tooling attacks (ATPA), in which the attacker develops a tool with a benign description, but reflects a fake error that cheat on sensitive data (such as SSH) to address the alleged question.
“As LLM agents become more capable and autonomous, their interaction with external tools through protocols, such as MCP, will determine how safe and reliably they work,” Kosman said. “Attacks of poisoning tools – especially advanced forms such as ATPA – put critical blind spots in modern implementations.”
That’s not all. Given that MCP allows AI (or assistant) agents to interact with different tools, services and sources of data consistently, any MCP client’s vulnerability can create serious safety risks, including manipulating data leaks or malicious code.
This is evidenced by the recently disclosed critical security lack in the popular Integration GitHub MCPWhich, if used successfully, can allow an attacker to steal the user’s agent through a malicious GITHUB problem and force it to drop data from private repositories if the user offers a “look at the problems”.
“The problem contains a useful load that will be performed by the agent as soon as the public repository is requested,” Mark Milanta and Luner-Kelner, researchers – NoteClassification of it as a case of an agent’s toxic flow.
Given this, the vulnerability cannot be resolved only by GitHub through the server’s side, as it is rather a “fundamental architectural problem”, which requires users to implement granulated permits to ensure that the agent has access to only those repositories that need to interact with and constantly check the interaction between agents and MCP systems.
Make a place to attack the MCP recovery
Fast climbing MCP as “connecting fabric for the automation of an enterprise and agency” also opened new attack avenues such as System Domain Name System (DNS) to access sensitive data by using the events using the server (Sse), the protocol used by the MCP servers to transfer the real -time communication mode for MCP customers.
Attacks DNS submerge Preparing a victim’s observer in the treatment of an external domain, as if it belongs to the internal network (ie Localhost). These attacks that are designed to bypass the policy of the same origin (Snot) Restrictions are caused when a user visits a malicious site created by an attacker through phishing or social engineering.
“There is a gap between the browser security mechanism and the network protocols,” Yaroslav Lobacevski Github – Note In an explanation by DNS Rebinding, published this week. “When the IP IP IPS is resolved, the web -page is changing, the browser does not take into account it and views the web page as if its origin has not changed. It may abuse the attackers”
This behavior, essentially, allows JavaScript on the client’s side from the malicious site to bypass security control and navigate other devices in the private victim network that is not subjected to public internet.
 |
| Attack MCP |
The MCP Rebind attack will take advantage of the controlled site controlled by the site, access the domestic resources on the local victim network to interact with the MCP server that works on Localhost via SSE and eventually allocate sensitive data.
“By abusing durable SSE connections, attackers can turn from an external phishing domain to navigate – Note in an analysis published last month.
It is worth noting that SSE was outdated on November 2024 in favor Lost http Of the risks that relate to the DNS Resind attacks. To mitigate the threat of such attacks, it is recommended to perform authentication on the MCP servers and confirm the “Origin” headline on all the incoming connections to the MCP server to make sure that requests come from trusted sources.