Google has entered to resolve the lack of security that could allow you to resolve your phone recovery number, potentially exposing their privacy and security risks.
The problem In the hall For Singapore, Brutecat security researcher uses the problem in the company’s recovery function.
Given this, using the loops of vulnerabilities on several moving parts, specifically focusing on the JavaScript-Disabled recovery version, which recovery of Google (“Google (.) Com/signin/Usernamerecovery”), which lacked a system designed to prevent spam.
The page in question is designed to help users check if the recovery number or phone number is related to a specific display name (such as “John Smith”).
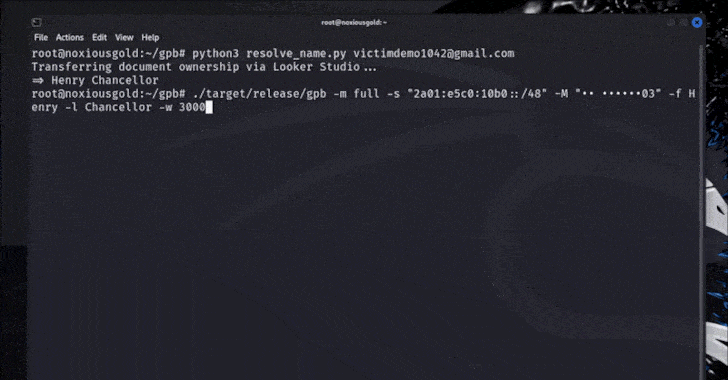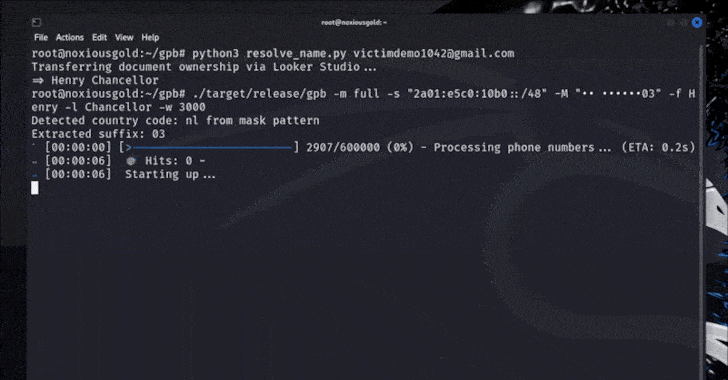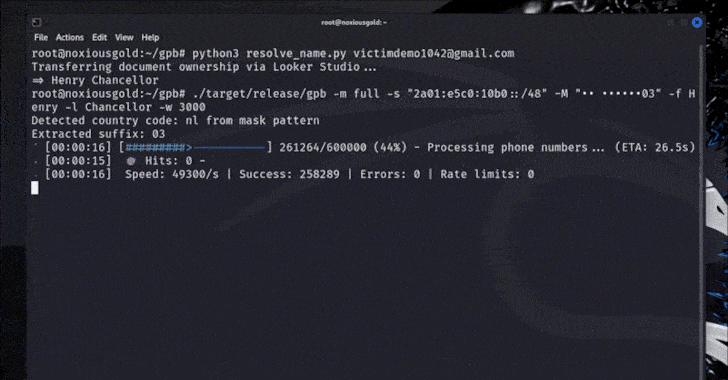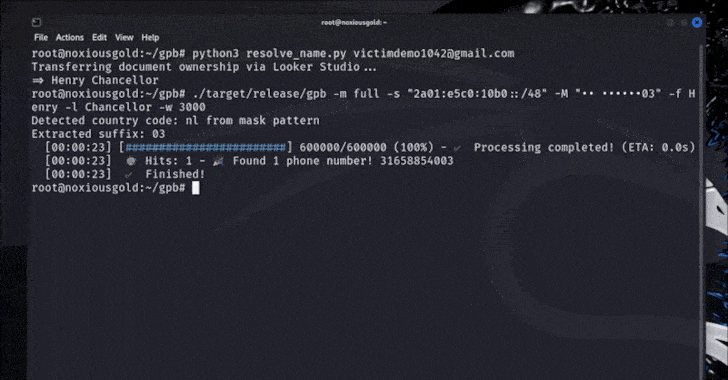
But the catch -based limited rate management eventually allowed to try all the reshuffle of the Google account number in the short period of time and come to the correct numbers per seconds or minutes, depending on the length of the phone number (which ranges from country to country).
The attacker can also take advantage of the forgotten Google password to find out the country’s country’s number -related victim’s phone number, and get their display name by creating A Looer Studio The document and the transfer of the victim’s ownership that actually forced their full leak on the main page.
In general, the feat requires the following steps –
- Labor
- Run the forgotten password stream for the target email address to get a camouflage phone number with the last two numbers reflected by the attacker (for example, •• •••• 03)
- Brown Power Phone number in relation
Brutecat said the Singapore number can be traced with the aforementioned equipment in 5 seconds, while the US number can be exposed in about 20 minutes.
https://www.youtube.com/watch?v=am3iplyz4sw
Armed with knowledge of the phone number associated with Google account, a bad actor can take control of it through it Attack to move SIM And eventually reset the password of any account associated with this phone number.
After the responsible disclosure of information on April 14, 2025, Google rewarded the researcher of $ 5,000, and connected the vulnerability, completely getting rid of a user recovery form that is not JavaScript, as of June 6, 2025.
The conclusions come in a few months after the same researcher minute Another 10,000 dollars exploit that the attacker could armed to expose the email address of any YouTube channel owner by attaching API YouTube and outdated web -api associated with a pixel voice recorder.
Then in March also Brutecat disclosed that can get email addresses belonging to the creators that are included in the YouTube partner program (Ypp) using the access problem at the final point “/Get_Creator_channels”, receiving a $ 20,000 reward.
“(An) problem with access control to /get_Creator_channels Channel Channel Contentownerasciation, leading to an e -mail disclosure via API Content ID, Google, Google – Note.
“The attacker, who has access to Google account, which had a channel that joined the YouTube Affiliate Program (over 3 million channels), can receive an email address, as well as the monetization details of any other YouTube partner.