Google revealed the details of the financially motivated threat cluster stating that he was “specializing” on voice phishing (AKA Vishing) aimed at violating copies of organizations for large -scale data theft and subsequent extortion.
Intelligence team at threat of technological giant tracks activity under nickname Unc6040which, according to his words Com.
“Over the past few months, UNC6040 has demonstrated repeated success in violation of networks, forcing him to bring himself to his support employee in a convincing telephone based on telephone engineering,” company company company – Note In a report that shared with Hacker News.
This approach, Google Group Group Group (GTIG), has benefited to cheat on English -speaking staff to perform a threat to the subjects or lead to valuable information such as powers that are then used to facilitate theft.
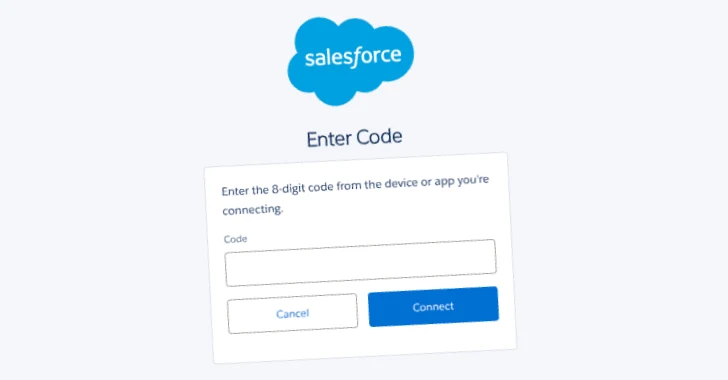
The characteristic aspect of the UNC6040 activity involves the use of a modified version of SalesForce’s Data loader that victims are cheating on the permit to connect to the Salesforce portal of the organization during an emergency attack. Data Loader is an app used to import, export and update the Salesforce platform.
In particular, the attackers direct the goal to visit the Salesforce page connected app and approve the modified version of the Data Loader application, which bears another name or branding (such as “my ticket portal”) from a legitimate colleague. This action gives them unauthorized access to the SalesForce customer environment and exfiltrate data.
In addition to losing data, the attacks serve as a UNC6040 stepping point to move toward the victim network, and then access and procurement information from other platforms such as OKTA, WorkPlace and Microsoft 365.
The selected incidents also participated in the extortion, but only “a few months” after observing the initial invasion, which testifies to the attempt to monetize and income from the stolen data, presumably in partnership with the second threat actor.
“During these attempts, the actor stated that the famous hacking groups Shinyhunters is likely as a method of pressure on their victims,” Google said.
UNC6040 intersect with computers related orientation to the powers of Okta and the use of social engineering via IT -support, the tactics that covered Scattered spiderAnother financially motivated actor of the threat that is part of the loose team.
Vishing did not go unnoticed by Salesforce, which in March 2025 warned of threatening subjects using social engineering tactics to present himself by IT staff on the phone and cheat on their customers in distributing their powers or approval of a modified data loader application.
“It is reported that they incur employees of our customers and third parties to the Phishing Pages, designed for theft of credentials and MFA tokens or forcing users to go to the Login.Salesforce (.) COM/SETUP/Connect to add an angry app”. – Note.
“In some cases, we have noted that the Data Loader app is a modified version of the Data Loader application and/or branding. Once the actor threatens access to the Salesforce customer, or adds an connected application, they use an connected application to avoid data.”
The development not only emphasizes the constant sophistication of social engineering companies, but also shows how IT support workers are increasingly directed as a way to gain original access.
“The success of companies such as UNC6040, using these exquisite VILing, shows that such an approach remains an effective threat vector for financially motivated groups seeking to violate organizational protection,” Google said.
“Given the long terms between the original compromise and the extortion, it is possible that in the coming weeks or months may face requirements for extortion in the coming weeks or months.”