Cybersecurity researchers have warned about a new phishing campaign that uses a legal remote access tool called Netbird to orientation on the main financial directors (financial directors) and financial executives in banks, energy companies, insurers and investment firms across Europe.
“In that, it seems, a multi -stage phishing operation, the attackers sought to expand Netbird, legitimate remote access to Vireguard’s based on the victim’s computer,” Trellix Srini Setopathy – Note In the analysis.
Activities, first discovered by cybersecurity company in mid -May 2025, was not related to a well -known actor or threat group.
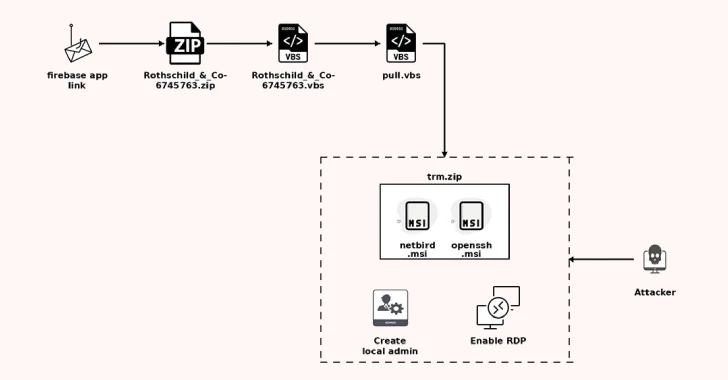
The starting point of the attack is a phishing -list that presents a recruiter with a Rothschild & Co. And he states that he offers a strategic opportunity in the company. E-mail is designed to attract recipients to the opening of the intended PDF attachment, which, in fact, is a phishing link that redirects them to the URL located in the Firebase app.
What is characteristic of the infection is that the true redirection URL is stored on the encrypted page and only available after the victim resolves the CAPTCHA check, which leads to the ZIP archive.
“The puzzle decision performs the function (JavaScript), which transcripts it with a solid coded key and redirects the user to a decrypted link,”-said Seethapathy. “The attackers are increasingly relying on these custom gates, hoping to promote the past protection that is already flowing phishing sites protected by Cloudflare Turnstile or Google Recaptcha.”
The archive contains the Visual Basic (VBScript) scenario, which is responsible for receiving the next VBScript stage from the external server and launching it through “wscript.exe”. Then this second stage VBScript loads another useful load from the same server, renamed it “Trm.zip”, and removes two MSI files: Netbird and Openssh.
The last stage involves the installation of two programs on the infected hoste, the creation of a hidden local account, allowing you to get remote access to the desktop and store Netbird with the planned tasks to automatically start on the system restart. The malicious software also removes any labels on the Netbird desktop to ensure that the victim is not revealed by a compromise.
Trellix stated that he determined another redirect URL, which has been actively working for almost a year, and serves the same useful VBScript load, which indicates that the company may have existed for a while.
The results once again show how there are opponents increasingly leaning On legitimate remote access applications such as Connectwise Screenconnect, Atera, Splashtop, Fleetdeck and Logmein, decide to set perseverance and use it to enroll in the victim, simultaneously evading the detection.
“This attack is not your typical phishing,” Seathopathy said. “It is well thought out, purposefully, subtle and designed to promote past technologies and people. This is a multi -stage attack when the opponent uses social engineering methods and protection evading to create and maintain sustainable access to the victim system.”
Disclosure of information is the same
- Attacks on it abuse A trusted domain related to the well-known Japanese Internet service provider (provider) to send phishing messages from the email address “Company@nifty (.) COM” in an attempt to check your email authentication and harvesting credentials
- Attacks on it abuse Google Apps Development Platform for Plating Phisching Pages that look legitimate and steal Microsoft accounting for login using baits with invoices
- Attacks on it imit Apple Pay account for theft of sensitive users, including credit card data and account data data
- Attacks on it abuse Working spaces concepts for conducting phishing pages that cheat on users by clicking the links that transfer the victims to the forged entry page in Microsoft under the guise of viewing the total document and the accounting of the credentials through the telegram
- Attacks on it surround Annual Lack of Security in Microsoft Office (Cve-2017-1188) For delivery option malicious software in shape, hidden in a fake PNG file and steal sensitive data from disturbed hosts
Phas Services Laine Bar
Conclusions also come as a trust wave, detail about operating ties between Tycoon and Dad (AKA PHOENIX) phishing kits, emphasizing their infrastructure overlapping and the use of centralized phishing infrastructure. Dadsec is the work of the actor threatening, which is monitored by Microsoft nicknamed Storm-1575.
“The infrastructure used by Dadsec is also related to the new company that uses the” Tycoon 2FA “platform” Phishing-A-Service (Phaas) “,” Trustwave Resist Cris Tomboc and King Orande ” – Note. “The Tycoon2fa Physhing Investigation shows how opponents continue to clarify and expand their tactics within the phisching-how’s ecosystem (Phaas).”
 |
| Operation Tycoon 2fa Phas |
The popularity of Phaas Services testifies to the emergence of a new “Chinese set” of the Chinese language, called Haozi, which estimated the criminal operations of more than $ 280,000 over the last five months, selling advertising for third participants. It works on the basis of 2000 dollars a year.
“Unlike outdated phishing kits that require attackers to configure scripts or infrastructure by hand, Haozi offers smoothly – Note. “Once the attacker acquires the server and introduces his credentials into the panel, phishing software is automatically installed without having to run a single team.”
‘This installation without friction contrasts with other Phaas tools such as AI-I-Enabled Darkula Suite where the minimum use of the command line is still required. “
In addition to supporting the administrator panel, which users can manage all their companies in one place, Haozi has found that it offers an advertising space as a mediator to connect phisching buyers with the services of other persons, such as SMS suppliers.
 |
| Dash Parnin Phishing Haozi |
Another aspect that distinguishes HAAZI from other kits is a special Telegram channel after selling (@yuanbaoaaaa) to help customers in debugging and optimizing their companies, placing it as an attractive option for beginners cyber criminals.
“As the enterprise security groups become more effective in detecting and solving penetration attempts, attackers unfold social engineering and phishing, a tactic that does not require a hardened perimeter,” said Netcraft researcher Harry Everett.
“Phaas offers reduce gender and large -scale automation and support companies. These new models function more than the SAAS business than the black market hacking groups, complete with subscription prices, customer service and product updates.”
Microsoft, in a consultation, published last week, showed how Phaas platforms are increasingly running the Phasing account on average (AITM) as adopting multifactorial authentication (Foreign Ministry).
Some other methods include Phishing device code; Oauth Campant PHING; Where the threat subjects use the Open Authorization Protocol (OAUTH) and send emails with a harmful link to the third party; The device joins phishing, where threatening subjects use a phishing link for the purpose of the trick in the resolution of the Domain-Jono device controlled by the actor.
The Windows manufacturer said he noticed the suspects in Russian subjects threats that use other applications or emails that refer to the upcoming meeting to provide a malicious connection that contains a valid permit code. The technique was First documented According to Volexity in April 2025.
“While both end users and automated security measures have become more able to determine malicious phishing investments and links, motivated threat subjects continue to count on the use of human behavior with convincing bait,” Igor Sakhnov, Vice President of Corporation and Deputy Ciso Identity, Microsoft, Microsoft, – Note.
“As these attacks depend on the deception of users, the training of users and the awareness of commonly identified social engineering methods are key to protecting them.”