Google on Wednesday revealed that a Chinese actor funded by a state known as APT41 used malicious software called ThuPPRogress, which uses Google Calendar for command and control (C2).
The technological giant, which revealed the activity in late October 2024, said that malicious software was carried out on the website of the compromised government and was used to orient for several other state organizations.
“Incorrect use of cloud services for C2 is a technique that many threats are used to combine with legitimate activity,” – Google Group Group (Gtig) Researcher Patrick Whitel – Note.
APT41, also tracked in the form of axioms, black, tiphun (formerly Bari), bronze atlas, side, sick, red kelp, ta415, wicked Panda and Winnti, the name intended for the prolific group of a national state known for its targeting of governments and organizations. and entertainment, technology and automatic sectors.
In July 2024. Google disclosed What several organizations operating in these industry verticals in Italy, Spain, Taiwan, Thailand, Turkey and the UK were aimed at a “sustainable company” using a combination of web and people such as AntSWord, Bluebeam, DustPan and Dustrap.
Then earlier this year was a subclass at the APT41 umbrella definite As a result of the attack on Japanese companies in the production, materials and energy sectors in March 2024 as part of the Revivalstone campaign.
The latest attack chain recorded by Google provides for sending emails containing a link to the ZIP archive, which is located on the operated government site. The Zip -Fale contains a directory and a Windows label (LNK), which is masked as a PDF document. The catalog presents seven different arthropod images (from “1.jpg” to “7.jpg”).
The infection begins at the launch of the LNK file, causing the PDF to be represented by the recipient, which states that the species extended from the directory must be announced for export. However, it should be noted that “6.jpg” and “7.jpg” are fake images.
“The first file is actually an encrypted useful load and deciphered by the second file, which is a DLL file, running when the target clicks on LNK,” said Waitl, adding malicious programs, implementing various methods of stelles and evading, such as useful loads, epiphosus.
The malicious software consists of three different components, each of which is deployed in the series and designed to perform a specific feature –
- Plusdrop, Dll, used to decrypt and perform the next stage in memory
- Plusinject that is running and performing The process is to allocate On the legal process of “svchost.exe” for the introduction of the final useful load
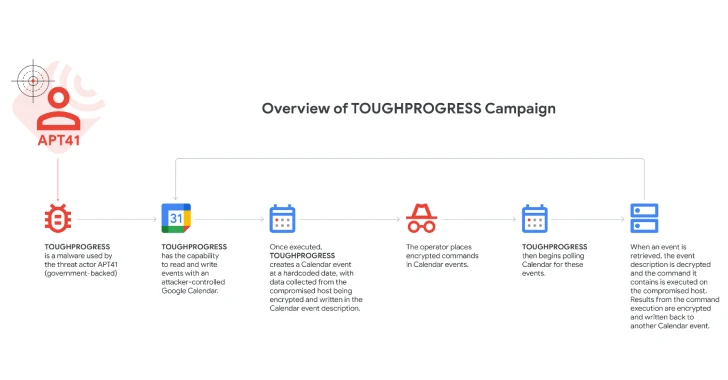
- HOLDPROGRESS, MAIN MOSSIBLE SOFT SOFT SOFT SOLDS FOR GOOGE CELENDAR FOR C2
Malicious software is designed to read and recording activities with a controlled Google Calendar attacker, creating a zero minute on a solid date (2023-05-30) to save the collected data in description of the event.
The operators encountered the teams in the calendar events on July 30 and 31, 2023, which were then interviewed by malware, deciphered on the compromised Windows hoste, and the results written back to another calendar event from which they can be obtained by the attackers.
Google said he took the step of removing the malicious Google calendar and stopped related work space projects, thereby neutralizing the entire company. It also states that the affected organizations were notified. The exact scale of the company is unclear.
This is not the first time APT41 has armed Google’s services to its advantage. In April 2023 Google disclosed The fact that the actor threatens is aimed at the unnamed Taiwanese Organization to deliver the Red Comening tool with the open source Go, known as Command and Control Google (GC2), put through passwords protected on Google Drive.
After installing the GC2, it acts as a back to read commands with Google Sheets and Exfiltrate data using the Cloud Storage service.