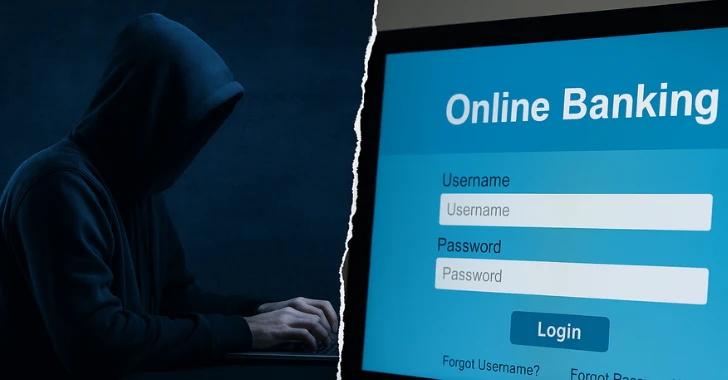
Do you expect the final user to enter the CyberCriminal computer, open your browser and enter their users and passwords? Hope not! But this will, in fact, happen when they are a victim of an attack in the browser on average (Bitm).
As on average (Mitm) attacks, Bitm sees how criminals look Data flow control between victim’s computer and target serviceAs researchers of the University of Sanalent Franco Thomas, Christian Catalan and Ivan Tarina outlined the document for the international magazine of information security. However, there are several key differences.
A person in the middle against the browser in medium
The MITM attack uses a proxy server that places itself between the victim’s browser and the legal target service at the application level. To place and start the victim’s computer requires some malware software.
But the attack by the other. Instead, the victim believes that they use their own browser – for example, to conduct regular online banking – if instead they actually work with a transparent remote.
As noted in the paper, it is as if the user “sat in front of the attacker’s computer, using the assailant keyboard,” that is, the attacker can fix, record and change the exchange between the victim and the service they receive.
Anatomy attacks rayme
So how does it work? A typical attack of the muzzle occurs in three stages:
- Phishing: The victim was deceived by pushing a malicious hyperlink that indicates the attacker’s server and authenticizes their web application.
- Fake browser: The victim is connected to the attacker’s server and with a transparent web browser through the malicious JavaScript insert. The attack will use programs such as Keyloggers to expand criminals to intercept and use the victim’s data.
- Earning for web -adjusts: The victim uses all his usual services on the Internet without realizing that they use a transparent browser. Now their powers are being subjected to the perpetrator.
Tokens session
Attack is working Setting tokens session. This allows the attackers to disrupt even multifactorial authentication (Foreign Ministry); After the user has completed his Foreign Ministry, the session token is usually stored in their browser. As noted by researchers from Google Mandiant subsidiaryIf the sign itself can be stolen, the Foreign Ministry no longer matters:
“The theft of this session token is the equivalent of the theft of the authentified session, that is, the enemy will no longer need to be called by the Foreign Ministry.” This makes the tokens a useful purpose for both red team operators – experiencing the protection of the system – and more anxious, real opponents.
Using the Bitm frame to focus on authenticated sessions, attackers enjoy the benefits of rapid targeting, as they can go to any web -site in seconds with a little configuration, Mandiant notes. When the application is oriented, the legal site is submitted through the browser controlled by the attacker, making the victim an extremely difficult to tell the difference between the real site and its counterfeit counterpart.
Cooks -files or tokens Oauth is lined just before encryption, while fast -expressive means that stolen tokens can be transferred to the turning servers in seconds.
Strategies mitigating the consequences
These complex attacks can cause significant damage, but there are ways to avoid or mitigate the consequences. At the widest level, users should always be extremely cautious by the links they may be looking at the site before clicking on any link. Here are some other options:
Passwords in a new era
The conclusion is clear: Bitm attacks can bypass traditional safety approaches, even allowing criminals to intercept names and passwords. So, does the passwords insignificant?
The answer is a loud “no”. By establishing multifactorial authentication (Foreign Ministry) — Including reliable passwords, you are still complicating life for cybercriminals, Especially if they don’t fix the marker session right away.
Even when the attackers become more sophisticated, you need to monitor the basics. Passwords remain a vital component of the Foreign Ministry – in fact, for most organizations, they are likely to remain the first defense line. Strous cybercriminals, protecting your passwords, no matter how they attack.
Password Policy Specups Provides your Active Directory Passwords touching zero. You can pursue a stronger password policy while constantly scanning your Active Directory on more than 4 billion compromised passwords. In combination with an effective Foreign Affairs, eg Special Access SpeckersYou will defend your end users both on the password and the entrance. Do you need security for the Ministry of Foreign Affairs or password? Refer to the chat.