Cybersecurity researchers revealed that the actor of the CodenaMent Vicvertrap has compromised almost 5,300 unique networking devices in 84 countries and turned them into a Honeypot network.
The actor threatens is observed using a critical lack of security that affects the Mater Bustion RV016, RV042, RV042G, RV082, RV320 and RV325 (CVE-2023-20118) to translate them into the Honeypots En Mass. Most infections are located in Macau, with 850 compromised devices.
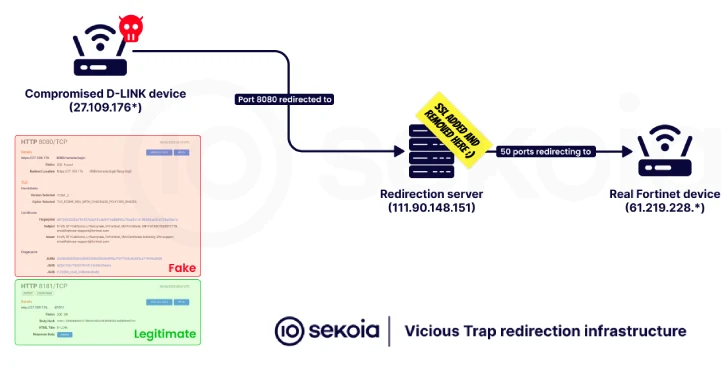
“The infection network includes the execution of the shell script, dubbed Netghost, which redirects incoming traffic from certain ports compromised router in infrastructure similar to Honeypot – Note in an analysis published on Thursday.
It is worth noting that the operation of CVE-2013-20118 was previously attributed to the French cybersecurity company of another botnet, called Polariz.
Although there is no evidence that these two sets of activity are connected, it is believed that the actor standing for Viciodtrap is likely to adjust the Honeypot infrastructure, breaking a wide range of online equipment, including SOHO, SSL VPNS, DVRS and BMC controllers with more than 50 brands, Araknis Nevers. ASUS, DS-LINK, LINKSYS.
“This installation will allow the actor to observe the attempts in several environments and potentially collect non-public or zero feats, as well as re-use of access obtained by other subjects,” he added.
The attack network entails weapons Cve-2023-20118 to download and execute Bash through FTPGE, which then turns to the external server to get WGET Binary. In the next step, Cisco’s lack is operated for the second time, using it to perform the second scenario obtained using the previously dropped WGET.
The script scenario of the second stage, which is internally called Netghost, is set up for redirecting network traffic from a broken system to a third -person infrastructure controlled by the attacker, thereby facilitating the enemy’s attacks on average (AITM). It also comes with the ability to remove itself from the broken host to minimize the medical examination.
SEKOIA noted that all attempts to exploit from one IP -Dar (“101.99.91 (.) 151”), with the earliest activity dating in March 2025.
“This assumption coincides with the use of the Netghost attacker,” said security researchers Felix Eima and Jeremy Tion. “The redirect mechanism effectively places an attacker as a silent observer, capable of collecting attempts to operate and possibly access to the web transit.”
As recently this month, exploitation efforts are also aimed at ASUS routers, but from another IP -Odars (“101.99.91 (.) 239”), although it was not revealed that the threat subjects create a single Honeypot on infected devices. All IP -Designs used in the company are located in Malaysia and are included in the autonomous system (AS45839), which is managed by the Shinjiru hosting provider.
The actor is believed to be a Chinese origin based on a weak overlapping with the gas infrastructure and the fact that the movement is redirected to numerous assets in Taiwan and the United States.
“The ultimate goal of Vicvertrap remains even incomprehensible (though) with high confidence that this is a Honeypot style net,” Socai summarized.