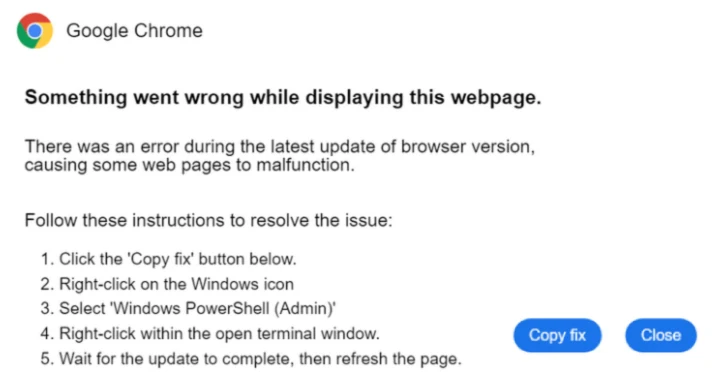
Malicious software known as Latrodectus became the last who accepted the widely used social engineering technique called Clickfix as a distribution vector.
” Technique Clickfix Particularly risky because it allows malicious software to perform memory rather than writing to the disk, ” – said the Exel in a report that is shared with Hacker News.
Latrodectus, which is believed to be the successor of ICEDID, is the name given to malicious software that acts as a bootler for other useful loads such as redemption. It was first recorded by Profpoint and Team Cymru in April 2024.
Incidentally, malicious software – one of the many malware affected by operational failure within the ENDGAME operation that remove 300 servers worldwide and neutralized 650 bumblebee domains, Lactrodectus, QAKBOT, Hijackloader, Danabot, Trickbot and Warmcookie between May 19 and 22, 2025.
In the latest set of Latrodectus attacks, which is observed by Expel in May 2025, unanswered users are deceived by copying and executing the PowerShell team from the infected site, a tactic that has become a widespread method of distributing malicious programs.
“When using users, these commands will try to install a file located on a remote URL using MSIEXEC and then execute it in memory,” the Eccal said. “This prevents the attacker from writing a file on a computer and a risk that is manifested by a browser or antivirus that can detect it on the disk.”
The MSI installer contains a legitimate application from NVIDIA, used to download malicious DLL, which then uses CURL to download the main useful load.
To mitigate the attacks of this type, it is recommended to disable the Windows Run program using group policy facilities (GPO) or exclude the “Windows + R” hot key by changing the Windows Registry.
From Clickfix to Tiktok
Disclosure occurs when Trend Micro discovered details of a new engineering company, which instead of leaning on fake CAPTCHA pages, use Tiktok videos that are probably generated using artificial intelligence tools (AI) to deliver Vidar and theft information, instructing users to manage from wicked commands, Microsoft Office, Capcut and Spotify.
These videos were posted from different Tiktok accounts such as @gitallowed, @zane.houghton, @allaivo2, @sysglow.wow, @alexfixpc and @digitaldreams771. These accounts are no longer active. One of the videos claiming to provide instructions as “instantly increased its Spotify experience” scored almost 500,000 views, with more than 20,000 likes and more than 100 comments.
The company notes ClickFix’s new escalation in that users looking for methods of activation of pirate applications are verbally and visually managed to open the Windows Run dialog by clicking on “Windows + R” Hot Key, run PowerShell and launch the team allocated in the video.
“Actors threatens now use Tiktok videos that are potentially generated using tools running on AI – Note.
“This company emphasizes how the attackers are ready to arm what the platforms in social media are currently popular for distributing malware.”
Fake Applications for Books used to steal seed phrases Mac
The resulting data also follows from the opening of four different malware that use the cloned version of the Live Live app to steal sensitive data, including seed phrases, to drain wallets from the cryptocurrencies of the victims. Activities continues Since August 2024.
Attacks use malicious DMG files that run Applescript for password exports and Apple Notes data, and then load the Training version of Ledger Live. Once the application is open, it warns users about the alleged account problem and that requires their seed phrase. The entered seminal phrase is sent to the server controlled attacker.
Moonlock lab that shed light on the company, stated disclosed from Jamf this month.
“The dark internet forums of the chatter around the Ledger schemes are growing. The next wave is already being developed,” the MacPaw Cybersecurity Department noted. “Hackers will continue to use the Trust CryPt owners in Ledger Live.”