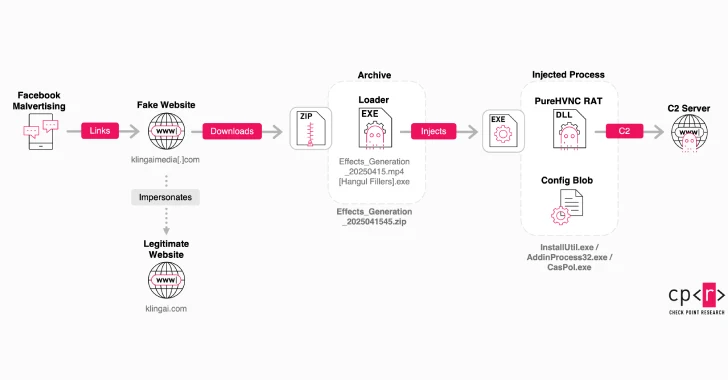
Fake Pages on Facebook and sponsorship on social media platforms are used to send users to false sites that disguise as AI sound For the purpose of deceiving the victims to download malware.
Kling AI-it’s Artificial Intelligence (AI) that works to synthesize images and videos from text and images. Launched in June 2024, developed by Kuaishou technology, which is located in Beijing, China. As of April 2025 data from the company.
“The attack used fake Facebook pages and advertising for distribution of a malicious file, which eventually led to the execution of Trojan remote access (rats), providing the strikers of remote control system and ability to steal sensitive data,” the check point – Note.
For the first time discovered in early 2025, the company leads anything suspicious users to a backed website such as Klingaimedia (.) CE or Klingaistudio (.) COM, where they are asked to create images or videos obtained by AI directly in the browser.
However, the web -sight does not generate multimedia as advertised. Rather, it offers an alleged image or video that is in reality is a malicious window hidden Filler Hangul (0xe3 0x85 0xa4) characters.
The useful load is included in the ZIP archive and acts as a forklift to launch a remote access and theft, which then establishes contact with the server team and control (C2) and credentials supported by the browser, session tokens and other sensitive data.
In addition to monitoring analysis tools such as Wireshark, Ollydbg, ProCmon, Procexp, Pestudio and Fiddler, make changes to the Windows register to set up persistence and run the second stage, introducing it into a legal process, such as “caspol.exe” or “allonutil.exe” for detection.
The second degree of useful load, embarrassed using .NETThis is a Purehvnc Rat, which contacts with a remote server (185.149.232 (.) 197) and comes with the ability to steal data from several cryptocurrency wallets installed in Chromium -based browsers. Purehvnc also accepts the plugin -based approach to make screenshots when jars and wallets are opened and a wallet.
Check Point said he identified at least 70 promoted posts from fake pages on social media representing themselves Kling AI. It is currently unclear who is behind the company, but the evidence has gathered from the web page fake site, and some ads show that they may be from Vietnam.
Using Malvertisise Facebook technology for distributing malware for theft has become a Vietnamese threat that was increasingly capitalization on the popularity AI generative tools push malicious software.
Previously this month Morphisec disclosed The fact that the actor of the Vietnamese threat uses fake tools working on AI as a bait to attract users to download the information theft of malicious software called Noodlophile.
“This company that represented itself Kling AI through fake ads and deceptive – Note.
“With the tactic, ranging from disguise files to remote access and theft, and signs indicating the Vietnamese threats groups, this operation fits into a broader tendency of increasingly targeted and complex attacks based on social media.”
Development occurs when the Wall Street Journal magazine report The meta fights with the “scammers’ epidemic when cyber -cuts flood Facebook and Instagram with different types of fraudsters, ranging from romance to sketch favorable ads to fake gifts. Many pages of scam work from China, Sri Lanka, Vietnam and Philippines, added in the report.
According to The rest of the worldFalse job ads TelegramFacebook and other social media are increasingly used to drive young Indonesians and getting counterfeit by Connecting scam In Southeast Asia, where they are forced to launch investment scams and fraudulent victims worldwide.