High-level state institutions in Sri Lanka, Bangladesh and Pakistan have been the goal of a new company organized by an actor threatened as a Sidgeinder.
“The attackers used phishing -electronic letters paired with a useful load of Geofed to ensure that only victims in certain countries have received malicious content,” – researchers of Acronis Santogo Pontiroli, Jozsef Gegeny and Prakas Thevendaran – Note In a report that shared with Hacker News.
Attack networks use speech-fitting calls as a starting point to activate the infection and deployment of well-known malware, called as theft. It is worth noting that Modus Operandi matches recent sidewalls documented Caspersorski in March 2025.
Some of the goals of the company, on Acronis, include a commission for regulating the Bangladesh, the Ministry of Defense and the Ministry of Finance; Pakistan Directorate for Indigenous Technical Development; and the Sri Lanka, the Ministry of Finance, the Ministry of Defense and the Central Bank.
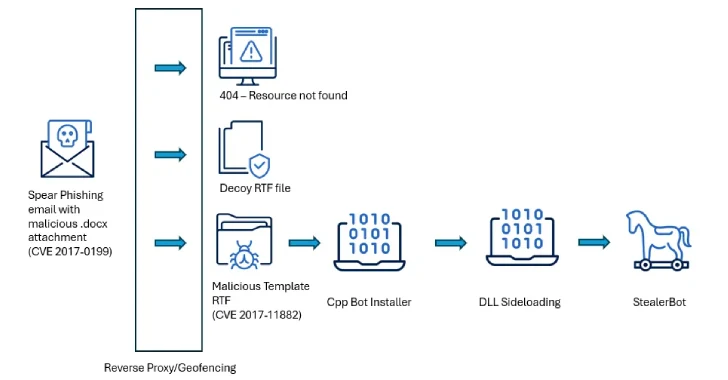
Attacks are characterized by the use of perennial drawbacks of remote code in Microsoft Office (Cve-2017-0199 and Cve-2017-1188) as the initial vectors for the deployment of malware capable of maintaining sustainable access in state conditions in South Asia.
The malicious documents when opening cause a feat for CVE-2017-0199 to deliver the useful load to the next stage responsible for installing Cteelerbot by using DLL download methods.
One of the characteristic tactics taken by the Boadkinder is that the e -mails with speakers are combined with a useful load to ensure that only victims that meet the criteria are malicious content. In case the IP IP is not the same, an empty RTF file is sent instead of the bait.
A malicious useful load-is the RTF file, which is armed with the CVE-2017-11882, a vulnerability of memory corruption in the Equity Editor, to launch a sherverbot-based Shercode loader.
According to Kaspersky, theft .NET implant This is designed to give up additional malware, run a backward shell and collect a wide range of data from disturbed hosts, including screenshots, pressing, passwords and files.
“Sidewinder has demonstrated consistent activity over time, maintaining a sustainable pace of operations without prolonged inaction – a model that reflects organizational continuity and sustainable intention,” the researchers said.
“More attentive analysis of their tactics, methods and procedures (TTPS) shows a high degree of control and accuracy, ensuring that the harmful useful loads will only be set for carefully selected purposes and often only for a limited time.”