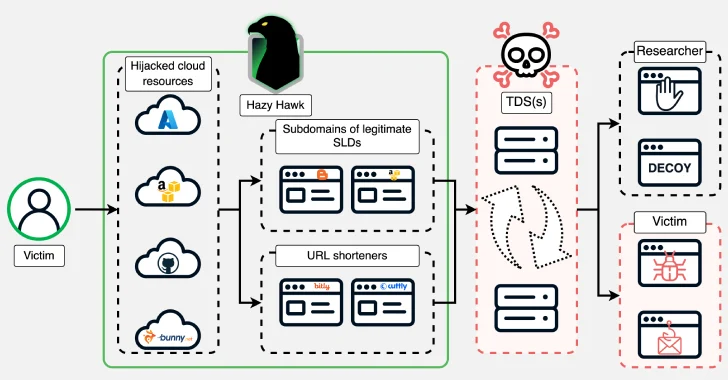
Actor threats known as A foggy hawk The abduction of abandoned cloud resources of high -profile organizations, including Amazon S3 Buckets and Microsoft Azure Finally, was noted, using incorrect setup settings (DNS).
Then the domain abductions are used to place the URLs that direct users to scams and malware using traffic distribution systems (TDSs), Infoblox reports. Some other resources, usurped by the actors, include those located on Akamai, Bunny CDN, Cloudflare CDN, GitHub and Netlify.
In February 2025, the DNS intelligence firm stated that she first discovered the actor threats after he received control over several sub-domains related to the US Disease Control (CDC).
Since then, other government agencies worldwide, well -known universities and international corporations, such as Deloitte, PricewaterHouscoopers and Ernst & Young, has been a victim of the same threat from December 2023.
“Apparently – Note In a report that shared with Hacker News.
“Instead, they feed on the Adtech underground semina, whisking the victims on a wide range of scrap and fake applications, and using the browser notifications to launch processes that will have a protracted impact.”
Hazy Hawk operations deserves attention – the abduction of trusted and reputable domains owned by legal organizations, which increases their authority in search results when used to maintain malicious and spamic content. But even more concerns, the approach allows the subject to bypass the detection.
At the heart of surgery is the ability of attackers to seize control over abandoned domains with hanging DNS Cname, technique Previously exposed Guard in early 2024 as exploited by bad actors to spread spam and press monetization. All you have to do from the threat is to register the missing resource to steal the domain.
The curious Hock is step further, finding abandoned cloud resources, and then ordered for malicious purposes. In some cases, the actor threatens the URL redirect methods to hide which cloud resource was hijacked.
“We use the Hazy Hawk name for this actor from the way they find, and the volume of cloud resources that have dnsya Cname Records, and then use them in the malicious URL distribution,” Infoblox said. “It is possible that the component is provided as a service and used by a group of actors.”
Attack networks often provide cloning the content of legitimate sites for its original site located on the stolen domains, with the victims to visit their pornographic or pirate content. The site visitors are then sent through TDS to determine where they landed on.
“Walking Hock is one of the dozen threatening subjects that we monitor the advertising partner world,” the company said. “The actors of the threat belonging to affiliate advertising programs lead users to individual malicious content and are stimulated to include requests to allow you to press notifications from” web -stytes “on the Redirect path.”
By doing this, an idea should Switch the victim’s device by pressing And to provide endless torrent malicious content, and each notice leads to different scams, terrible and fake surveys, and is accompanied by requests to allow additional notifications.
To prevent and protect against foggy hawks, the domain owners are advised to delete the DNS Cname Recording as soon as the resource is closed. The final user, on the other hand, is recommended to deny the notification requests from the websites they don’t know.
“While operators, such as Hazy Hawk, are responsible for the original bait, the user who presses, leads into the maze sketch and open malicious Adtech. The fact that Hazy Hawk has made considerable efforts to find vulnerable domains, and then using them for scams, Infoblox.