ASUS released updates to address two security deficiencies that affect the ASUS DriverHub, which, if successfully used, can allow the attacker to use the software to achieve the remote execution of the code.
Driver This is a tool designed to automatically detect a computer’s maternity board model and displaying the necessary drivers updates for subsequent installation by communication with A with A with A A highlighted site Located in “DriverHub.Asus (.) Com.”
Disadvantages found in the software given below –
- Cve-2025-3462 (CVSS Assessment: 8.4) – Vulnerability of Error Verification, which can allow unauthorized sources to interact with software features using the developed HTTP requests
- Cve-2025-3463 (CVSS Assessment: 9.4) – Incorrect Certificate Valmation, which can allow unreliable sources to affect the system behavior using the developed HTTP requests
The Mrubra’s security researcher, which is attributed to the identification and report on two vulnerabilities, said they could be used to achieve the remote code implementation as part of the attack on one click.
The attack network essentially includes the deception of the unsuspecting user for visiting DriverHub.Asus (.) Com (eg DriverHub.Asus.com.
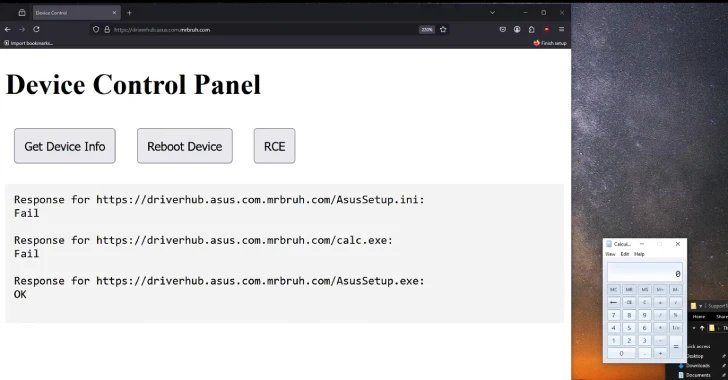
“When performing asussetup.exe, he first reads with asussetup.ini, which contains metadata about the driver,” the researcher interpret In a technical report.
“If you run asussetup.exe with the flag -s (DriverHub calls it using it to make a silent installation), it will perform everything shown in Silentinstallrun. In this case, the Ini file determines the CMD scenario that performs an automated driver installation, but it can start everything.”
All the attacker needs to successfully pull out the operation – this is the creation of the domain and place three files, the harmful useful load that will be launched, the modified version of asussetup.ini, which has the “Silentinstallrun”, installed in malicious binary and asussetup.exe.
Following the responsible disclosure of information on April 8, 2025, the questions were recorded on May 9. There is no evidence that vulnerabilities were used in the wild.
“This update includes important security updates, and ASUS strongly recommends users to update the Asus DriverHub installation to the latest version,” the company – Note In the newsletter. “The latest software update can be obtained by opening the Asus DriverHub by clicking the” Update “button.