The national actor threats known as Mirror The deployment of malicious software, called Roamingmouse, was noted as part of a cyber -scalp campaign against government agencies and government agencies in Japan and Taiwan.
The activity revealed by Trend Micro in March 2025 provided for the use of possessive affiliations to provide an updated version of the back called Anel.
“Anel file of 2025, reviewed in this blog, implemented a new team to support BOF (File File Becon) in memory,” Hara Hiroa Safety Researcher – Note. “This company is also potentially used Ball To launch the second stage of the back day noopdoor. “
The Chinese actor threatens, also known as the ground porridge, is evaluated as a subconductor within APT10. In March 2025 ESET shed light The company, which is called the Akairyū operation, which is aimed at the diplomatic organization in the European Union in August 2024 with Anel (aka the top incision).
Earning for various Japanese and Taiwanese structures indicates further expansion of their traces as hacking is committed to theft promote your strategic goals.
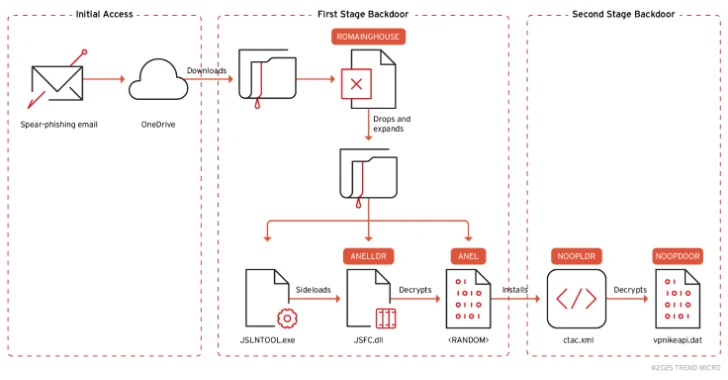
The attack begins with the e-mail with the Physhing-Nekatoria from which are sent from legitimate but invested accounts-which contains the built-in URL Microsoft OneDrive, which in turn loads the mailing file.
ZIP archive includes Excel document to be malicious software Roaming This serves as a pipeline to deliver components related to Anel. It is worth noting that roamingmouse has been used using Mirrorface since last year.
“Then the Roymingmouse deciphered the built -in mail file using Base64, lowers Zip and expands its components,” said Hiroaki. This is included in –
- Jslntool.exe, jstiee.exe, or jsvwmng.exe (legitimate binary)
- Jsfc.dll (Anelldr)
- Encrypted useful load aneel
- Msvcr100.dll (legal dependence on execution))
The ultimate goal of the attack chain is to launch a legal executable file using Explorer.exe, and then use it to download the malicious DLL, in which case Anelldr, which is responsible for the transcript and launch of Anel Backdoor.
What is characteristic of Anel’s artifacts used in the company 2025 —This adding a new team to support memory execution Beacon’s facilities (Bofs) consisting of CE programs designed to expand Cobalt Strike with new features after operation.
“After installing the Anel file, the actors for the ground received screenshots using the Backdoor team and reviewed the victim’s environment,” Trend Micro explained. “It seems that the opponent is investigating the victim by viewing screenshots, launched processes and domain information.”
Selected specimens also used an open source tool called Sharphide to launch a new noopdoor version (aka Hiddenface), a different back day that was previously used as used Hacking Group. Implant, on its part, supports DNS-Over-HTTPS (Roof) To hide the IP address during team and control operations (C2).
“The land of the porridge still remains an active stable threat, and now aims at government agencies and state institutions in Taiwan and Japan in its latest campaign, which we found in March 2025,” said Hiraki.
“Enterprises and organizations, especially those who have high-value assets, such as sensitive data regarding management, as well as intellectual property, infrastructure data and access accounts must continue to be vigilant and implement active safety measures to prevent cyber-fad sacrifice.”