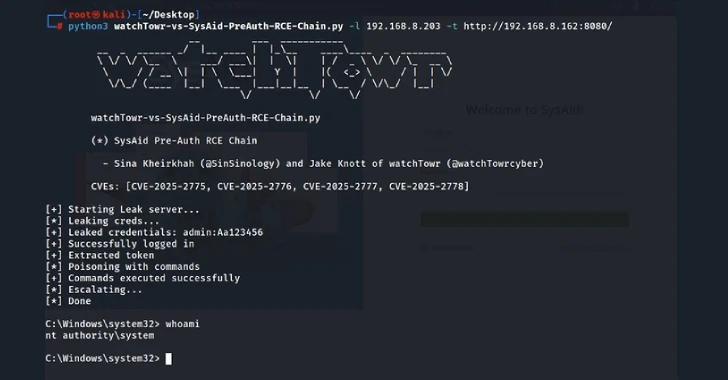
Cybersecurity researchers have revealed several disadvantages of safety in the Sysaid IT Support software that can be used to achieve pre -proven remote code with high privileges.
The vulnerabilities tracked as CVE-2025-275, CVE-2025-2776 and CVE-2025-2777 were described as the external essence of the XML (XXE) Injections that occur when the attacker is able to successfully interfere with the analysis of the XML app.
This, in turn, can allow the attackers to introduce dangerous XML subjects into the web application, allowing them to make fake a server request (Ssrf) Attack and in the worst cases removed code.
Description of three vulnerabilities, In the hall To observe the laboratories, Sina Heerha and Jake Nett researchers are the following –
- CVE-2025-2775 and CVE-2025-276-WHO DESTRY XXE within /MDM /Checkin Endpoint
- CVE-2025-277-pre-presented XXE within the final point /LSHW
Labs Watchtowr described vulnerabilities as trivial for operation using a specially designed HTTP Post at the final point.
Successful exploitation of deficiencies can allow the attacker to obtain local files containing confidential information, including the Sysaid “Initaccount.cmd”, which contains information about the administrator account name and the password of the simple text created during the installation.
Armed with this information, the attacker can gain complete administrative access to Sysaid as a user recognized by the administrator.
Worse, the disadvantages of the XXE can be attached to another vulnerability of the command operating system, the third part-time persons-for-achievement of the remote code. The problem of command injection was assigned to the ID Cve-2025-277.
All four vulnerabilities were corrected With the help of Sysaid with release on the premises of the version 24.4.60 B16 in early March 2025. made available.
With security deficiencies in Sysasaid (Cve-2013-47246) exploited According to the redemption of actors such as the CL0P, in the attacks with zero day, it is necessary for users to update their copies to the latest version.