Cybersecurity researchers revealed three security deficiencies in Standpoint The Ruby web server interface, which, if successfully used, can allow the attackers to gain unauthorized access to files, enter harmful data and reinforce magazines under certain conditions.
Vulnerability named According to the Cybersecurity supplier Opswat, below –
- Cve-2025-27610 (CVSS assessment: 7.5) – vulnerability of the path that can be used to access all files in the indicated
- Cve-2025-27111 (CVSS’s assessment: 6.9) – Incorrect Carbage Failure (CRLF) sequences and incorrect output neutralization for vulnerability of logs that can be used to manipulate log records and log files
- Cve-2025-25184 (CVSS Assessment: 5.7) – Incorrect Carriage Failure (CRLF) and Incorrect Output for Vulneration Magazines that can be used to manipulate log records and injection of malicious data
Successful exploitation of disadvantages can allow the attacker to darken traces of attacks, read arbitrary files and enter a malicious code.
“Among these vulnerabilities, the CVE-2025-27610 is particularly serious, as this can allow an unauthorized attacker to receive confidential information, including configuration files, credentials and sensitive data that will lead to data violations,” Popwa said in a report that is shared with Hacker NEWS.
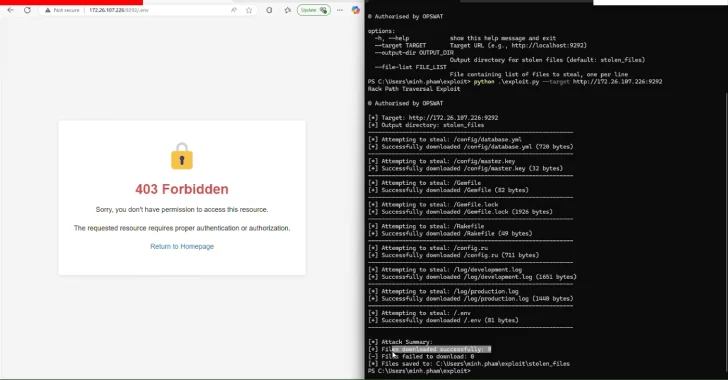
Disadvantages follow from what Stop :: staticThe intermediate software used to maintain static content, such as JavaScript, styles and images tables, does not start the pathways provided by users before submitting the files that will lead to the script if the attacker can provide a specially designed way to access files outside static files.
“In particular, if the parameter: the root parameter is not clearly defined, the default racks are the value for the current working catalog, assigning it the value dir.pwd, implicitly designating it as a root directory for web catagories,” said OPSWAT.
As a result, if the parameter: the root version is either uncertain or incorrectly configured with respect to the option: URLS, an unauthorized attacker can equip the CVE-2025-27610 through the methods to access sensitive files outside the designated web catalog.
To mitigate the risk that is deficiency, it is recommended to upgrade to the latest version. If immediate correction is not an option, it is recommended to remove the use of the rack :: static, or make sure the root: points on the way directory containing only files that need to be addressed publicly.
Critical Lack of Infodraw Media Related
Disclosure of the information occurs as a safety defect that was found in the Infodraw Media Relay Service (MRS) that allows you to read or delete arbitrary files using the passage of the passage (CVE-2025-43928, CVSS: 9.8) in the user’s Logn page.
Infodraw is an Israeli Mobile CCTV manufacturer used to transfer audio, video and GPS data on telecommunications networks. As depending on Web -Sight CompanyIts devices are used by law enforcement agencies, private investigations, fleet management and public transport in many countries.
“The grass path of the vulnerability allows it to read any file from the systems for unauthorized attackers,” said security researcher Tim Philip Scheffers in a statement shared with Hacker News. “In addition, there is a” vulnerability of a file “that allows the attackers to delete any file from the system.”
A drawback that allows you to log in to the username “../../../../,” affects both Windows and Linux versions of the MRS. Given this, the deficiency continues to be unwavering. The vulnerable systems in Belgium and Luxembourg were accepted offline after the responsible disclosure of information.
“The affected organizations first recommend accepting the application offline immediately (because, despite the early warnings, the manufacturer’s patch is not available, and it is believed that the vulnerability will be operated by malicious subjects in the near future),” Philip Schaepers, – Note.
“If it is not possible, the systems should be further protected by additional measures (such as using VPN or a specific IP unlock).”