A critical lack of security was disclosed at the Commvault Command Center, which can allow the code arbitrary to enforce the affected institutions.
Vulnerability tracked as Cve-2025-34028It carries the CVSS 9.0 with a maximum of 10.0.
“The setting of the command center revealed a critical safety vulnerability, allowing remote attackers to perform an arbitrary code without authentication,” Commvault – Note In an advisory order published on April 17, 2025. “This vulnerability can lead to a complete compromise in the team center.”
This affects the release of innovation 11.38 from versions 11.38 to 11.38.19 and was resolved in the following versions –
Researcher Watchtowr Labs Sonya McDonald, who is credited – Note In a report that is shared with Hacker News that it can be used to achieve a pre -proven remote code.
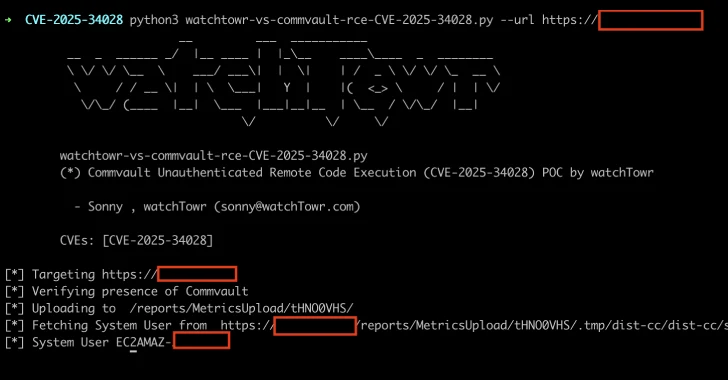
In particular, the problem is rooted at the final point called “Deploybpackage.do”, causing what is called a pre -maneuated server request (Ssrf) Due to the fact that “there is no filtering as to what hosts can be reported.”
More worse, SSRF’s deficiency can be converted to achieve the code using the ZIP archive file containing the malicious file .jp. The whole sequence of events looks the following –
- Send the HTTP request to the /commandcenter/deploywebpackage.do, causing the Commvault instance to receive a mailing file from the external server
- The ZIP -Fail content will be laid out into the .tmp catalog under the control of the attacker
- Use the Servicepack parameter to translate the .TMP directory into the check -ups on the server
- Complete SSRF via /commandcenter/deploywebpackage.do
- Complete the shell with the /reports/metricsUpload/hell/.tmp/dist-cc/dist-cc/shell.jsp
Watchtowr also created Identification of the generator of the artefact What organizations can use to determine whether their instance of vulnerability is.
With vulnerability in backup and replication software like Dream and Nakivo When you come under active exploitation in the wild, it is important that users apply the necessary softening to protect against potential threats.