Named new Android Marsware Platform (MAAS) (MAAS) Supercard X can promote communication close fields (Nfc) Attacks of the relay, which allows cybercriminals to conduct fake hammer.
The active company focuses on banking institutions and card issuers in Italy in order to compromise payment card data, said the firm prevention firm. There are data that suggest that the service is moving on Telegram.
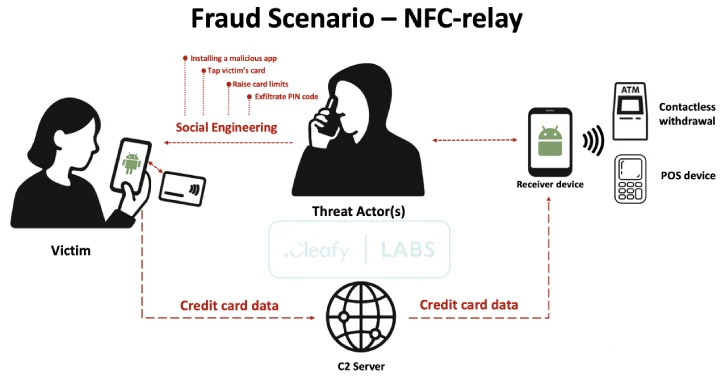
Supercard X “uses a multi -stage approach that combines social engineering (via Sming and theheng call), malicious app installation and interception NFC data for highly efficient fraud”, Federico Valentini Safety Researchers, Alesandra and Michel Rovila – Note.
The new Android malicious software, the work of a Chinese -speaking actor threats, is distributed by three different fictitious applications that are exposed to installing them through social engineering technologies such as deceptive SMS or WhatsApp reports –
- Verifica Carta (io.dxpay.remotenfc.supercard11)
- Supercard X (io.dxpay.remotenfc.supercard)
- Kingcard NFC (io.dxpay.remotenfc.supercard)
Messages are presenting alerts about the safety of the banks to cause a false sense of relevance, calling the recipients to call a specific number to challenge the transactions.
Then the infection chain goes to what is called a phone -delivery phone (frog), where the actors threaten the victims to install the app under the guise of safety software through direct telephone conversations. It was also found that the threat entities use a convincing tactic for the victims and instructed them to remove any existing card restrictions, allowing them to easily drain the means.
The operation is based on previously unregistered relay technique, which allows the subject of the threat of falsification of payments (POS) and automated machines for machines (ATMs), intercepting and relaying NFC communications from infected devices.
To do this, the attackers urge the victims to bring their debit or credit card in close physical intimacy to their mobile device, allowing Supercard X malicious software to fix the transmitted card data and transfer them to the external server. Then the information about the prepared map is used on the device that is controlled by the threat to unauthorized transactions.
An application that extends to the victims to capture NFC data cards is called the reader. A similar app, known as TAPPER, is installed on the actor threat to the card information. The connection between the reader and the TAPPER is carried out using HTTP for command and control (C2) and requires the login system.
As a result, it is expected that the threat entities create an account in the Supercard X platform before distributing malicious applications, after which the victims were instructed to enter credentials to enter it during a phone call.
This step serves as a key shroud in the overall attack because it establishes a connection between the victim’s infected device and the TAPPER Actor Actor, which allows the card data to be transmitted for subsequent cash exits. The TAPPER app is also intended to imitate the victim card using stolen data by deceiving POS Terms and ATMs to recognize it as a legitimate card.
The artifacts of the “reader” malicious programs, identified by Cleafy, tolerate subtle differences on the entry screen, indicating that they are assemblies created by affiliate actors to adapt the companies according to their needs. In addition, Supercard X uses mutual TLS (Mtls) To ensure communication with its infrastructure C2.
This threat of subjects may cheat on anything suspended users who change critical settings over phone calls did not go unnoticed by Google that there is said it works On a new Android feature that effectively blocks users to install applications from unknown sources and providing accessibility services.
Currently, there is no evidence that SuperCard X is distributed through the Google Play store, users are advised to study the descriptions of applications, permits and reviews before loading them. It is also recommended to keep Google Play Protect, which includes devices from new threats.
“This Romanesque company imposes a significant financial risk that goes beyond the normal goals of banking institutions to touch on the suppliers of payments and credit card issuers,” the researchers said.
“The innovative combination of malicious programs and the NFC relay gives an opportunity for attackers to carry out fraudulent cash with debit and credit cards. This method demonstrates high efficiency, especially when orientation to ATMs contactless.”