Russian loud hacking group called Redcurl He was associated with the ransom company for the first time, which notes the departure on the “threat of the actor”.
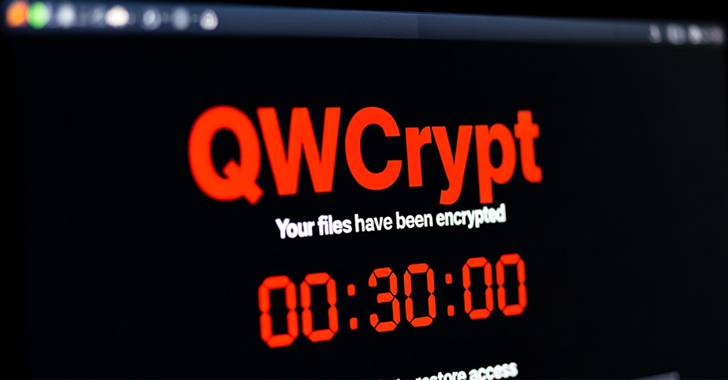
Activity observe The Romanian Bitdefender Cybersecurity Company provides for the deployment of never seen a ransom, called QWCRIPT.
RedcurlThey are also called the Earth Capr and the Red Wolf, has the history of the orchestration of corporate attacks aimed at different structures of Canada, Germany, Norway, Russia, Slovenia, Ukraine, the United Kingdom and the United States. It is known that it has been actively operating since November 2018.
Chains of attacks documented According to Group-IB in 2020, the use of possessive sheets containing personnel resources (HR) to activate the process of deployment of malware. Earlier this January hunting minute The attacks set by the actor threatened to several organizations in Canada to deploy a loader called Redloader with “simple back” capabilities.
Then last month Canadian Cybersecurity Company Esentire disclosed Using Redcurl Spam PDF attachment is masked as resume and accompanying letters in phishing messages to download malicious forklift software using the legitimate Adobe “AdnotificationManager.exe”.
The sequence of the attack, the detailed Bitdefender, traces the same stages, using files with a mounted images (ISO), masked into resume to start a multi -stage infection procedure. In the image of a disk that mimics the Windows Savior Savior (SCR) is the binary AdnotificationManager.exe used to perform the loader (“Netutils.dll”) by downloading dll.
“After the shooting of netutils.dll, she immediately launches a Sherlexecutea call with an open verb by sending the victim’s browser at https://secure.indeed.com/auth,” said Martin Tsugiak, director of technical decisions at Bitdefender, in a report that shared with Hacker News.
“This reflects the legitimate” Really “page, calculated by a distraction intended for misleading the victim, thinking they just open a resume. This social engineering tactic gives a window to work malicious software.”
 |
| Image Source: Esentire |
Forklift, for the Bitdefender, also acts as a download for the next DLL stage, as well as setting stability on the host through the planned task. Then the recently received dll is performed by means of the program compatibility (pcalua.exe), technique minute According to Micro trend in March 2024.
Access provided by the implant opens the way for lateral motion, allowing the actor threatening to move on the network, collect exploration and even more escalate their access. But it seems that the main turn from the established Operandi regime, one of these attacks also led to the deployment of redemption.
“This purposeful targeting can be interpreted as an attempt to maximize the damage with minimal effort,” Tsugiak said. “Having encrypted virtual machines located on hypervisers, making them unsolvable, Redcurl effectively disables the entire virtual infrastructure, affecting all the services located.”
The software is executed, in addition to using your own vulnerable driver technique (BYOVD) to disable the final points software, takes measures to collect system information before running the encryption procedure. What’s more, the ransom note decreased after encryption appears to be inspired by LockBit, Hardbit and Mimic.
“This practice of reshuffling the existing redemption text raises questions on the origins and motivations of the Redcurl group,” Zuggek said. “In particular, there is no well -known special leak site (DLS) associated with this compelling way, and it remains unclear whether the note is about buying a true extortion or sabotage.”