The threatening scaffolds have discovered a new threatening actor called UAT-5918, which attacks Taiwan in Taiwan’s critical infrastructure since at least 2023.
“Uat-5918, actor threats that are believed – Note.
In addition to critical infrastructure, some other targeted verticals include information technology, telecommunications, academies and health care.
Say uat-5918 is said Volts typhoon. Flax typhoon. Tropical landing. Land estriaand Dalbit.
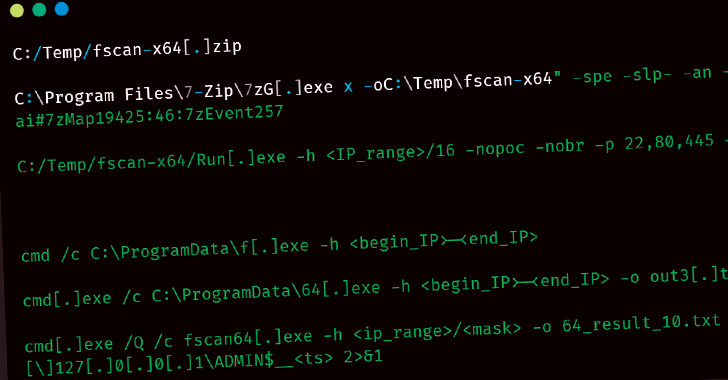
The attack networks organized by the group provides for its initial access, using the N-day security deficiencies in unprocessed Internet servers and applications that are exposed to the Internet. The fixing is then used to discard several open source tools for network intelligence, system information and lateral motion.
A UAT-5918 representative after operation involves the use of a quick reverse proxy (Frp) and NEO-REGEORGE to set up back proxy tunnels to access the final points using remote hosts controlled by the attackers.
The threatening actor also uses tools such as Mimikatz, Lazagne and the Browser’s Flower, called the browserdattalit to collect the credentials for further committing deep into the target environment via RDP, WMIC or impact. Also used is Chopper Web Shell, Crouperoor and Sparrowdoor, the last two of which have previously been used by another threatening group called Earth Estries.
In particular, the browsdattat is designed to record information, cookies and viewing history from web browsers. The threatening actor is also involved in the theft of systematic data, listing local and general discs to find interesting data.
“The activity we have monitored suggests that the activity after the compromise is carried out by hand, and the main purpose is the theft,” the researchers said. “Obviously, this also includes the deployment of web shells in any domain-detected and internet servers to open several entry points to the victim organization.”