Agency for cybersecurity and US infrastructure (CISA) has added Lack of safety at high speed affectingShip) Catalog, citing evidence of active exploitation.
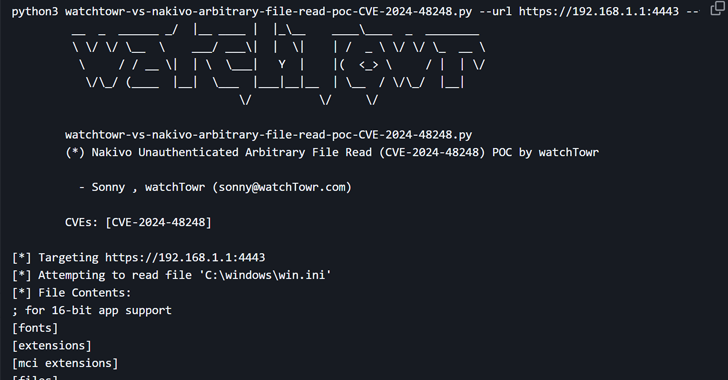
The vulnerability in question is the CVE-2024-48248 (CVSS: 8.6), an absolute traverse mistake that can allow you to read files on the target host, including sensitives, such as “/etc/shadow” through the endpoint “/c/rm.”. This affects all versions of the software to version 10.11.3.86570.
“Backup and replication Nakivo contains the absolute path of vulnerability that allows the attackers to read arbitrary files,” Cisa said in the advisory.
Successful lack of lack can allow the enemy to read secret data, including configuration files, backups and credentials that may act as a stepping stone.
There is currently no details about how vulnerability is used in the wild but development occurs after passing Labs publish proof of concept (Poc) Operate by the end of last month. The question was address As of November 2024 with the version v11.0.0.88174.
In addition, the cybersecurity firm noted that the vulnerability of reading an arbitrary file of an unauthorized file may be armed to obtain all the stored credentials used by the Nakivo target and located in the Product01.H2.DB database.
Kev also added to the KEV directory – two other disadvantages –
- Cve-2015-1316 (CVSS assessment: 9.3) -edimax IC-7100 IP camera contains a command team vulnerably due to improper input, which allows the attacker to achieve a remote code by using specially designed requests (does not request because of the device that reaches the end of life)
- Cve-2017-12637 (CVSS assessment: 7.5) – SAP Netweaver Application Server (AS) Java contains A Vulnerability of the passage of catalogs In Planning/UI/JS/FFFFFFFFFFFBCA41EB4/UIUTILJAVASScriptjs, which allows the remote attacker to read arbitrary files through .. (point) in
Last week Akamai disclosed This CVE-2025-1316 is armed with bad actors for orientation on the default camera to deploy at least two different Botten Mirai options since May 2024.
In light of the active operation of the Federal Civil Executive Agency (FCEB), the necessary mitigations should be applied by April 9, 2025 to provide their networks.