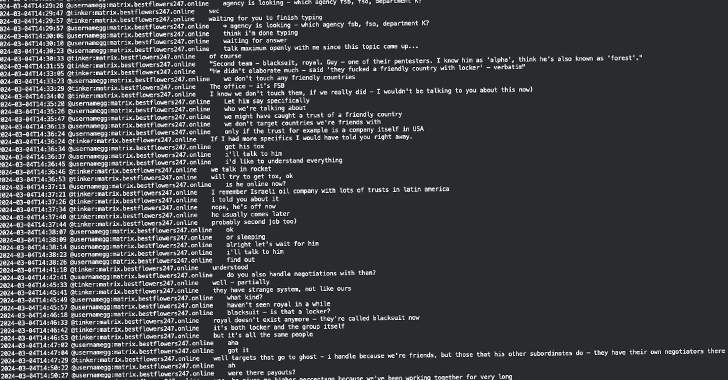
Recently Leak Chat internal magazines Among the members of the Black Basta Ransomware Operation found possible links between the gang of electronic crimes and the Russian authorities.
A leak containing more than 200,000 reports from September 2023 to September 2024 was published by Telegram @Exploitwhispers.
According to the analysis of the Cybersecurity Company Trellix, allegedly leader Black Basta Oleg Nefedov (aka GG or AA) may have received assistance from Russian officials After his arrest In Yerevan, Armenia, in June 2024, which allowed him to escape in three days.
In GG reports he claimed to contact high -ranking officials to go through the “green corridor” and promote prey.
“This knowledge of chat leaks burden Black Basta Gang completely giving up – Note.
Among other notable conclusions that include –
- The group most likely has two offices in Moscow
- The group uses Openai Chatgpt to make fraudulent official letters in English
- Some group members intersect with other extorting operations as Rub and Cactus
- Developer Fierce This is a Ukrainian citizen who goes on the Internet -Pseudonim Mecor (aka N3auxaxl), and that to develop a loading message on malware, Black Basta was required in the year QakbotFailure
- Group rented A dark shield from Rastafareye and used theft Lumma to steal credentials as well as additional malicious programs
- The group developed a frame after operation and control (C2) called Breaker to establish persistence, evasion and maintain access to network systems
- GG worked with Mecor over New Ransomware, which comes from the original code, which led to the release of a prototype written in C, which testifies to possible rebranding efforts
Development comes when ECLEcticiq has discovered the work of Black Basta over a rough frame called Butbed, which is designed to perform automated online scanning and credentials against edge network devices, including widely used firewalls and VPN solutions in corporate networks.
There are data that suggest that the CyberCrime crew uses a PHP platform since 2023 to carry out large -scale credentials and gross attacks on target devices, allowing the threat to the subjects to get visibility on the victim networks.
“Brutus Basis allows Black Basta branches to automate and scale these attacks, expanding your victim pool and accelerating monetization to manage the extorting operations,” Horde Bujakai’s security researcher – Note.
“Internal communication shows that Black Basta has greatly put into a brutal frame, which allowed the fast scanning of the Internet network and large-scale accounting for focus on weak passwords.”