Cyber -esproys are becoming more and more perfect, and traditional safety approaches are struggling to keep up. Organizations can no longer rely on periodic estimates or static vulnerability lists to remain safe. Instead, they need a dynamic approach that provides real -time understanding as the attackers move on the environment.
There are attackers schedules here. After taking the potential attack paths, they offer a more strategic way to identify and mitigate the risk. In this article, we will study the benefits, types and practical application of attack schedules.
Understanding the tiers of the attack
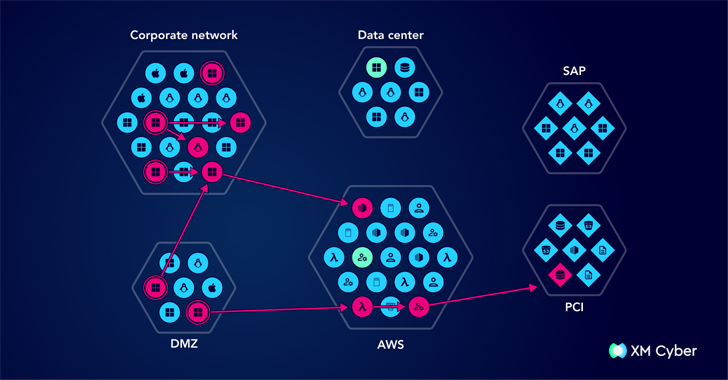
The graph of the attack This is a visual idea of the potential pathways of the system or the network. It reflects how the attacker can move through different weaknesses – incorrect configurations, vulnerabilities and powers, etc. – To achieve critical assets. Attack schedules can include data from different sources, constantly updated as the environment changes and model the real world attack scenarios.
Instead of focusing solely on individual vulnerabilities, attack graphs provide a greater picture – as different gaps in safety, such as incorrect configurations, credentials and network exposure, can be used together to create a serious risk.
Unlike traditional security models, which prefer vulnerabilities based only on severity results, attack graphics in operation and business impact. The reason? Only because the vulnerability has a high CVS score does not mean that this is an actual threat to this environment. The attack schedules add a critical context, showing whether vulnerability can be used in conjunction with other weaknesses to achieve critical assets.
The attack schedules can also provide constant visibility. This is, unlike disposable estimates, such as red tests to combine or penetration that may quickly become out of date. Analyzing all the possible ways that the attacker can pass, organizations can use attack schedules to determine and solve “Drops” – key flaws, which, when fixed, significantly reduce the overall risk.
Types of attack graphs explained
All the attack schedules are not equal. They are in different forms, each with its strengths and restrictions. Understanding these types helps security teams choose the right approach to detect and mitigate the risks.
Security schedules
Security schedules reflect relationships between different elements of the system such as user resolutions, network configurations and vulnerability. They provide the visibility of how different components are connected. However, they do not show how the attacker can use them.
- Plus – Security schedules are relatively simple to implement and provide valuable information in the organization’s infrastructure. They can help security groups identify potential safety spaces.
- Downside – They require manual requests to analyze risks, that is, security teams should know what to look for in advance. This can lead to missed attacks, especially if several weaknesses are combined in unexpected ways.
General graphs
General schedules combine data from multiple safety tools such as vulnerability scanners, identity management systems and cloud security solutions into a single model.
- Plus – They use existing safety tools, providing a more holistic understanding of the risk in different conditions.
- Downside – Integration can be a difficult task with potential data and visibility jogging. Because these graphs rely on individual tools with their own restrictions, the overall picture may still be incomplete.
Schedules of holistic attacks
Graphs of advanced and holistic attacks Take another direction. They are designed to model the attacker’s behavior in the real world, with particular emphasis on how threats develop in different systems. They reflect all possible attack ways and constantly update themselves as the environment changes. Unlike other schedules, they do not hope for manual requests and pre -specified assumptions. They also provide constant monitoring, real exploitation context and effective priority – which helps first and foremost security team focus on the most important risks.
Practical advantages
Attack schedules provide constant visibility on the attack that offers a security team dynamic, a view -view view, rather than obsolete shooting from periodic estimates. Having reflected how attackers could potentially navigate the environment, organizations will get a more accurate understanding of developing threats.
They also improve the priority and management of risk through the contextualization of vulnerabilities. Instead of blinding the high-level CVS deficiencies, security teams can determine critical stifling points, which, when fixing, significantly reduce the risk on several attacks.
Another major advantage is cross communication. The attack schedules simplify the complex security problems, significantly helping CISO overcome the problem of explanation for leaders and councils through clear visual ideas.
Finally, the attached schedules increase the efficiency of restoration efforts, ensuring that security groups focus on providing first critical business. Priority in determining fixes based on both actual exploitation and business impact, organizations can effectively distribute security resources.
Using an attack schedules for active safety
The attack schedules transfer cybersecurity from a reactive position to an active strategy. Instead of waiting for the attacks to take place or rely on rapidly paid estimates, security teams can use attack schedules to anticipate threats before being operated.
The key element of this transition from jet to active safety is the ability of the attack schedules to integrate the threat. Constantly including data on new vulnerabilities, operating methods and the behavior of the attacker, organizations can remain ahead of threats rather than respond after harm.
The constant assessment is also crucial in modern IT -years, where changes are the norm. Attack schedules provide real -time updates. This helps security teams adapt to both networks, identity and cloudy environments. Unlike static models, attack graphs offer constant visibility on the way of attack, allowing you to be smarter, more informed by decision -making.
Using attack schedules, organizations can go beyond traditional vulnerability to focus on real -world and business impact. This transition from reactive correction to a strategic risk reduction makes safety surgery more effective and effective. Ultimately, the attack schedules allow teams to close the critical gaps in security, strengthen the defense and remain in front of the opponents.
Note: This article is written by Menachem Shafran, SVP strategies and innovation, and Tobias Traebing, VP Global Sales Engineering, on XM Cyber.