The new company focuses on the company in Taiwan with malicious software known as Winos 4.0 Within the framework of phishing emails, which are masked as the National Taxation Bureau of the country.
A company found last month’s Fortinet Fortiguard Labs, notes out of previous attack chains that used malicious apps related to games.
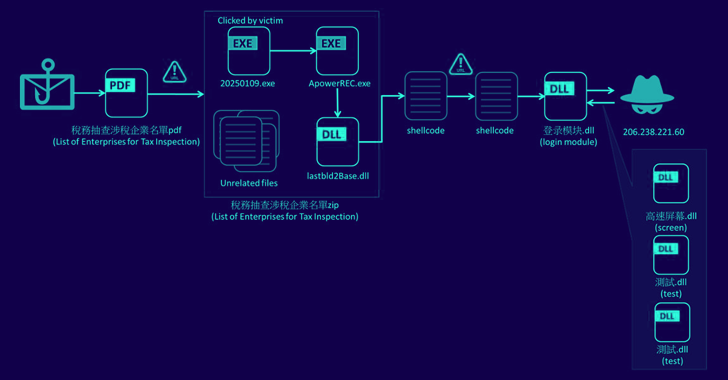
“The sender claimed that the malicious file was a list of enterprises planned for the tax inspection and asked the recipient to transfer the Treasury information,” the security researcher Pai Khan Liao – Note In a report that shared with Hacker News.
The investment is an official document of the Ministry of Finance, urging the recipient to load a list of enterprises planned for the tax inspection.
But in reality, the list is a Zip -Fail that contains malicious dll (“lastbld2base.dll”), which will laid the basis for the next stage of the attack, leading to the execution of Shellcode, which is responsible for loading the Winos 4.0 module from the remote server (“206.238.221 () 60”) for the collection.
The component described as an entry module, is able to do screenshots, write the keys, change the contents of the clipboard, monitor connected USB -devices, start Shellcode and allows you to perform sensitive actions (such as cmd.exe) when the safety with Kingsoft and Huorong will be displayed.
Fortinet said he also watched the second attack chain loading Internet Modul This can do screenshots WeChat and Internet Bank.
It is worth noting that A set of invading Distribution of malicious Winos 4.0 software has been assigned Monikers Void Arachne and Silver Fox, and malicious software is also overlapped Another Trojan Remote Access tracked as Valleyrat.
“They both come from one source: GH0St Rat, which was developed in China and opened in 2008,” said Daniel Dos Santos, Head of Security Studies at Vedere Freescout Lab, The Hacker News.
“Winos and Valleyrat are variations of the GH0St rats attributed to silver fox by various researchers at different times. Winos was a name that is commonly used in 2023 and 2024, while Valleyrat is now used.
ValleyratIt was first identified in early 2023, recently observed using counterfeit chrome sites as a pipeline to infect Chinese -speaking users. Similar boot schemes were also used to deliver GH0St rats.
In addition, the Attack Winos 4.0 chains included what is called Cleversoar’s mount, which is performed using a MSI installation package, distributed as fake software or game -related apps. Also fell with Winos 4.0 via Cleversoar is an open source code Nidhogg Rootkit.
“Cleversoar (…) installer checks the user language settings to make sure noted At the end of November 2024. “If the language is not recognized, the installer stops, effectively preventing the infection. This behavior strongly indicates that the actor threatens first and foremost focuses on victims in these regions.”
The disclosure of information occurs when Silver Fox APT was associated with a new company that uses the Training Players Dicom viewers to expand Valleyrat, which is then used to reset and cryptocurrencies on the victims. It is noteworthy that attacks use a vulnerable version Truesight driver To disable antivirus software.
“This company uses Dicom Treanized Viewers as Launches to Infect Victim Systems (Valleyrat) for remote access and control, key to capture the activity and powers of users, as well as a cry -to -use systemic resources for financial benefits,” the enterprise ” – Note.