A new malware company focused on Edge device from Cisco, ASUS, Qnap and Synology was noted to redo them into a botnet called Polaredge at least from the end of 2023.
French Cybersecurity Company SEKOIA – Note It observed unknown threats that use Cve-2013-20118 (CVSS rating: 6.5), a critical lack of security that affects Cisco Small Business RV016, RV042G, RV082, RV320 and RV325, which can lead to arbitrary commands on sensitive devices.
The vulnerability remains unwavering due to the status of routers reaching the end of life (EOL). According to the softening, Cisco recommended in the early 2023 to make the deficiency mitigated by disabled remote control and blocking to ports 443 and 60443.
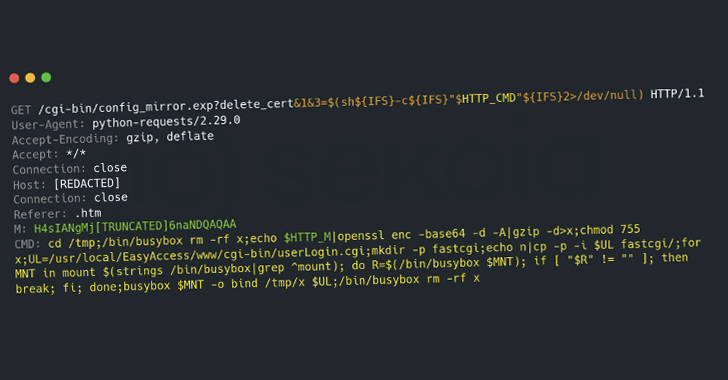
In an attack registered on Honeypots Sekoia, vulnerability was said to be used to provide previously unregistered implant, Backdoor TLS, which includes the ability to listen to incoming customers and perform teams.
Backdoor is launched by a shell called “Q”, which is obtained through FTP and launched after successful vulnerability. This comes with capabilities –
- Cleaning log files
- Stop suspicious processes
- Download a malicious useful load called “T.Tar” from 119.8.186 (.) 227
- Complete the binary called “Cipher_log” extracted from the archive
- Set the stability by changing the file named “/etc/flash/etc/cipher.sh” to run binary “cipher_log”
- Complete “Cipher_log”, Backdoor TLS
CodenaMent Polaredge, malicious software enters the endless cycle by installing the TLS session, as well as the spawning process to manage customer requests and commands using Execmand.
“Binary informs the C2 servers that it has successfully infected the new device,” said SEKOIA Jeremy Zion and Felix Aim. “The malicious software transmits this information to the reporting server, allowing the attacker to determine which device is infected via IP -Drass/mating port.”
Further analysis revealed similar useful POLAREDGE loads used for targeting ASUS, QNAP and Synology devices. All artifacts were loaded in Virustotal by users located in Taiwan. Useful loads are distributed through FTP using IP -Drace 119.86 (.) 227 owned by Huawei Cloud.
Overall, according to the estimates, a botta worldwide compromised 2117 unique IP, most infections found in the US, Taiwan, Russia, India, Brazil, Australia and Argentina.
“The goal of this Botten has not yet been determined,” the researchers noted. “The purpose of POLAREDGE can be controlling the violated edge devices, turning them into operating boxes to launch offensive cyber -cars.”
“Botnet uses several vulnerabilities for different types of equipment, emphasizing its ability to focus on different systems. The complexity of useful loads further emphasizes the complexity of the operation, believing that it is performed by qualified operators.
Disclosure occurs when the Securityscorecard showed that a massive botten containing more than 130,000 infected devices armed for large -scale password disclosure attacks on Microsoft 365 (M365). Non -intellectual inputs with basic authentication.
Non -intellectual inputs are commonly used to verify authenticity and outdated protocols such as POP, IMAP and SMTP. In many configurations, they do not cause multifactorial authentication (Foreign Ministry). The main authentication, on the other hand, allows you to transmit data in open text format.
Activities are probably the work of the Chinese group, thanks to the use of the infrastructure associated with CDS Global Cloud and Ucloud HK, use stolen information from Infosteeler logs in a wide range of M365 accounts to obtain unauthorized access and sensitive data.
“This technique bypasses the modern entry protection and evades the Foreign Ministry, creating a critical blind place for security teams,” the company – Note. “The attackers use stolen credentials from InfosteAler magazines to systematically target accounts.”
“These attacks are recorded in non -interactive magazines that often ignore security groups. Attackers use this gap to conduct high -grade spray attempts that are not detected. This tactic has been observed in several M365 tenants worldwide, indicating a widespread and permanent threat.”