The script (XSS) vulnerability in a virtual excursion was armed with angry actors to introduce malicious scenarios on hundreds of sites for the purpose of manipulating search results and faring the company advertising campaign.
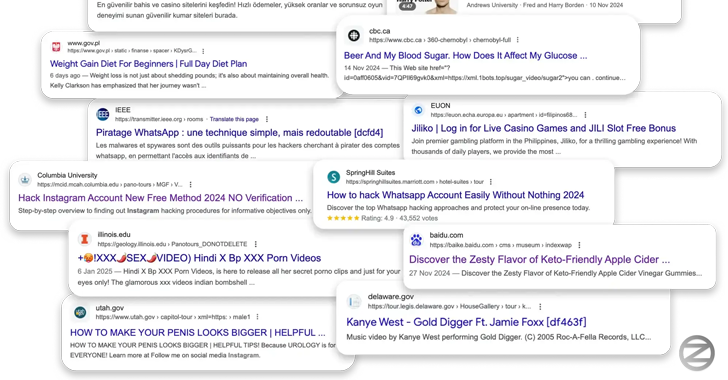
Safety Researcher Oleg Zaitsev in a report that is shared with Hacker News, said the company was named 360xss – More than 350 websites are affected, including state portals, US state -owned sites, US universities, large hotel networks, newsletters, car shows and several Fortune 500 companies.
“It wasn’t just spam -operation,” – the researcher – Note. “It was an industrial abuse of trusted domains.”
All these sites have one thing in common: a popular base called Krpano This is used to install 360 ° images and videos to facilitate interactive virtual tours and VR.
Zaytsev said he came across the company after he got into pornography related to the pornography listed in Google’s search, but with a domain associated with Yale University (“Virtual.quantuminstrate.yale (.) Edu”).
A noticeable aspect of these URL is the XML parameter, which is designed to redirect the site visitor to the second URL, which belongs to another legal site, which is then used to perform a useful load coded64 through XML document. The expanded useful load for its part delivers the target URL (ie ad) from another legal site.
The XML parameter transmitted to the original URL, which is provided in the search results, is part of the wider configuration setting specified “PassqueryParameters“It is used if Built -in Krpano Panorama Viewer into the HTML page. It is specifically designed to transfer HTTP parameters from URL to view.
The security problem here is that if the option is included, it opens the door to the script when the attacker can use a specially created URL to perform the malicious scenario in the victim’s web browser when a vulnerable site visits.
Really, a reflected the lack of XSS As a result of this behavior was disclosed in the Krpan at the end of 2020 (Cve-2020-24901CVSS’s assessment: 6.1) that testifies that potential for abuse It was publicly known for more than four years.
While the update entered in version 1.20.10, limited “PassqueryParameters”, in the list of permits to try to prevent such XSS -databilities, he found that clearly adding XML to the Allowlist list again introduced the risk of XSS.
“From version 1.20.10, the default installation was not vulnerable,” said the Hacker News researcher. “However, the PassqueryParameter setting in conjunction with the XML parameter allowed the XML’s external configuration through the URL, which led to the XSS risk.”
“The operated versions I meet were first and foremost the older, pre -predicted version 1.20.10.”
According to Zaitsev, the company used this weakness to abduction more than 350 sites to serve sketching ads related to pornography, dietary supplements, internet cosino and fake news sites. Moreover, some of these pages were armed to enhance video views on YouTube.
The company deserves attention, not least because it abuses trust and authority of legal domains to detect significantly in the search results LIFT Optimization Search System (SEO)Which, in turn, is carried out by abuse of the XSS deficiency.
“The XSS reflected is a fun vulnerability, but it independently requires users’ interaction, and one of the biggest problems is to make people press your reflected XSS link,” Zaitsev said. “So the use of search engines as a distributed platform for your XSS is a very creative and steep way to do it.”
After the responsible disclosure of information, the latest issue of Krpano eliminates the support of the external configuration using the XML parameter, thus softening the risk of XSS attacks, even if customization is used.
“Improved security Embedpano () PassqueryParameters: Data-Curl and external URL are usually not allowed because parameters and URL values for the XML parameter are limited within the structure of the current folder, according to Notes about the release For version 1.22.4 released this week.
It is currently unknown who is behind the mass operation, although abuse of the announcement as a monetization strategy.
Krpano users are advised to update their settings to the latest version and install “PassqueryParameters” on False. The affected websites are recommended to find and remove infected pages through Google search console.