Opposition activists in Belarus, as well as Ukrainian military and government organizations are the purpose of a new company that uses documents that are involved Picassoloader.
The cluster threats are evaluated as an extension of a long -standing company installed by an actor erected in Belarus know To match the Russian interests of security and the promotion of stories criticized by NATO.
“The company has been preparing since July-August 2024 and entered the active phase in November-December 2024,”-Researcher Sentinelone Tom Hegel – Note In a technical report that is shared with Hacker News. “The latest samples of malware and infrastructure activity (C2) (C2) show that the operation remains active in recent days.”
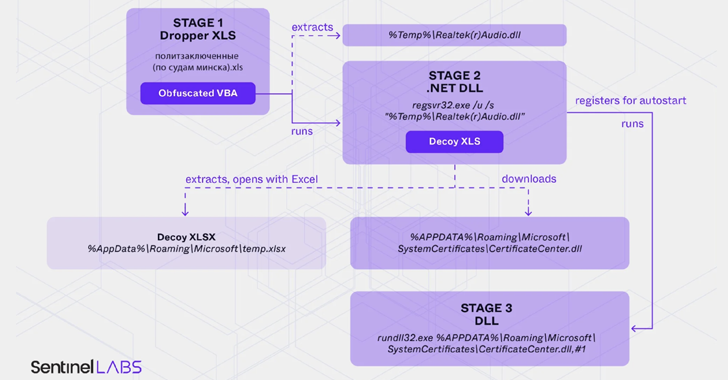
The starting point of the attack chain analyzed by cybersecurity company is the general document of Google Drive, which came from the account named Vladimir Nikifarech and accepted the RAR archive.
The rats file includes a malicious book Excel, which when opening the enchanting macro when the future victims allow you to launch macros. Macros continues to write the dll file, which eventually opens the way for a simplified version Picassoloader.
The next step in the system display the Exceel Excel file, while the background additional useful loads are loaded into the system. Recently in June 2024 this approach was used To deliver the cobalt after operation.
Sentinelone said she also discovered other Excel armed documents that carry baits with Ukraine’s theme to get an unknown malicious second -stage software from a remote URL (“Sciencealert (.) Store”) in the form of a seemingly harmless image JPG, technology, technique, technique, technique, technique Known as stegography. URL -Dour is more unavailable.
In another case, the Excel document registered BOOBY is used to deliver DLL called Libcmd, which is designed to launch cmd.exe and connect to Stdin/Stdout. It is directly loaded in memory in the form of .NET and executed.
“During 2024, the ghost repeatedly used the combination of Excel workbooks containing vba macro containing macro containing macro, and dropped built -in .net Downloaders, embarrassed. Confuserexsaid Hegel.
“While Belarus is not actively involved in military campaigns in the war in Ukraine, cyber -defeat actors associated with this do not have a spanning reservation against Ukrainian purposes.”