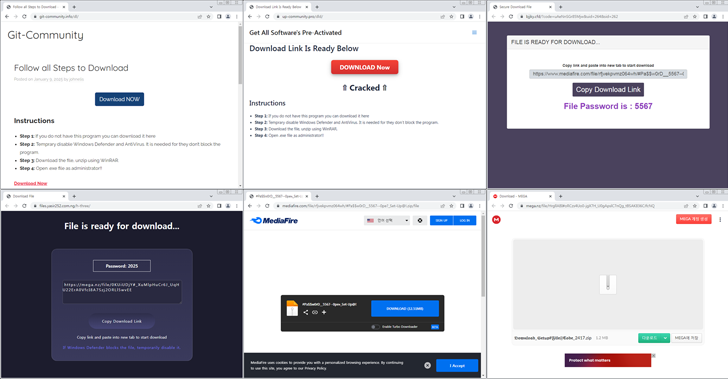
Cybersecurity researchers warn of a new company that uses hacked software versions as bait for the spread of information thefts such as Lumma and ACR thefts.
AHNLAB Safety Intelligence Center said he had observed the spike in the ACR’s theft of theft since January 2025.
A noticeable aspect of malicious software for theft is the use of technology called Detolish Dead Drop To get the actual command and control server (C2). This includes reinforcing on legal services such as Steam, Telegram’s Telegraph, Forms Google and Google Slides.
“The actors threaten the actual C2 domain in coding Base64 on a specific page,” ASEC – Note. “Malicious software gets access to this page, disassemble the string and receives the actual C2 domain address to perform malicious behavior.”
ACR theft, earlier common With the help of malicious loading software with Hijack is able to collect a wide range of information from impaired systems, including files given by web browser and expansion of the cryptocurrency wallet.
Development occurs when ASEC has opened another company that uses file expansion, which can be made by the Microsoft Management Console (MMC) to deliver Rhadamanthys Sorting for theft.
“There are two types of malware MSc: One uses vulnerability apds.dll (CVE-2024-43572) and the other performs the team” Teams “using the Taskpad console, a South Korean company engaged in a South Korean company – Note.
“The MSc file disguised in the MS Word document.” When the “Open” button is pressed, it downloads and performs the PowerShell scenario from the external source. The PowerShell loaded scenario contains the EXE (Rhadamanthys) file. “
Cve-2024-43572, also called GrimresourceThe Elastic Security Lab was first recorded in June 2024, which was operated with angry actors as a zero day. It was Latch From Microsoft in October 2024.
Were also malicious programs observe Using chat support platforms such as Zendesk, masking as customers to fool unsuspecting support agents to load the theft called Zhong Ctyler.
According to a recent report published by Hudson Rock, the computers have been infected over the past few years, which has led to corporate powers and session cookies, which can then be sold to cybercriminals on underground forums by other actors for profit.
Buyers can equip access provided by these powers for their own action after operation, which will lead to serious risks. These developments serve in order to emphasize the role played by malicious software for theft as The initial access vector This provides an attachment to a sensitive corporate environment.
“For a total of $ 10 for the magazine (computer) cybercriminations can acquire stolen data from employees working in classified defense and military sector,” Hadson Rock – Note. “The Infosteeler Intelligence is not just about finding out who is infected with the understanding of the full network of compromised powers and third risks.”
Over the past year, the threats have also increased the efforts to distribute different families of malware, including theft and remote access of Trojans (rats), through technology called Clickfix This often entails user redirect to fake CAPTCHA checking pages, entrusting them with copying and performing the PowerShell capricious commands.
One such useful load – this I2prrwhich uses the i2p anonymization network to anonymous the final C2 server.
“Malicious software is an advanced threat consisting of several layers, each of which includes complex mechanisms,” Sekoia – Note. “Using an anonymous network complicates tracking and prevents the value of the threat and spread in the wild.”