The threats of the actors standing for RansomHub It was noted that the Ransomware-How’s Service Scheme (RAAS) is observed using security deficiencies in Microsoft Active Directory and Netlogon protocol for escalation of privileges and obtaining unauthorized access to the domain victim network controller within its strategy after the complex.
“RansomHub has sent more than 600 organizations worldwide, covering sectors such as health care, finance, government and critical infrastructure, firmly establishing it as the most active ransom group in 2024,” IB-IB analysts ” – Note In an exhaustive report published this week.
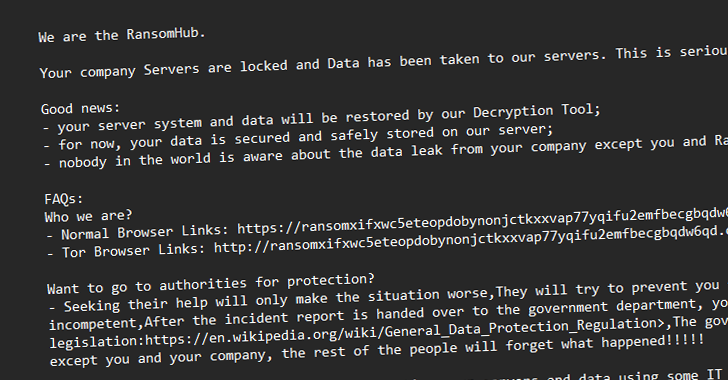
Group Ransomware first appeared In February 2024, having acquired the source code associated with the already non -existent knight (previously Cyclops) Raas Gang from the cyber -help forum to speed up his activity. About five months later, the updated version of the locker was advertised in the illegal market with the possibilities to remove data encryption through the SFTP protocol.
It comes in multiple variants that are able to encrypt files on Windows servers, VMware ESXI and SFTP. RansomHub is also observed actively gaining affiliates from Lockbit and Blackcat in the partnership program, which indicates an attempt to take advantage of law enforcement agencies aimed at its competitors.
In the incident analyzed by the Singapore Cybersecurity Company, an actor threats that sayCve-2024-3400) Using public proof of the concept (POC) before ending the victim network with the help of a rough force on the VPN service.
“This attempt was based on the enriched dictionary of over 5,000 users and passwords,” the researchers said. “The attacker eventually gained access through the default account, which is often used in the data backup decisions and the perimeter was finally broken.”
The initial access was then abused to attack the redemption, and the data encryption and the Experience occurred within 24 hours after the compromise.
In particular, it provided arms of two known security shortcomings in Active Directory (Cve-2021-42278 AKA NOPAC) and Netlogon Protocol (Cve-2020-1472 aka Zerologon) To seize control over the domain controller and carry the side movement across the network.
“The exploitation of the aforementioned vulnerabilities allowed the attacker to receive full prevailing access to the domain controller, which is the nervous center of the Microsoft Windows infrastructure,” the researchers said.
“Upon completion of operational operations, the attacker prepared the environment for the final phase of the attack. The attacker acted to make all the data of the company stored on various NAS at all unreadable and inaccessible, as well as inadmissible to restore, to force the victim to pay back to return his data.”
Another noticeable aspect of the attack is the use of PCHUNTER to stop and bypass the final points security, as well as Filezilla for data exports.
“The origins of Ranshub, its offensive operations and its blocked characteristics with other groups confirm the existence of a vivid ecosystem of cybercrimination,” the researchers said.
“This environment blooms on shared use, re -use and rebranding tools and source codes, nourishing a reliable underground market, where loud victims, shameful groups and significant money play the central roles.”
Development occurs when the cybersecurity firm spoke in detail about the internal work of “Grozny RAAS” known as VelxBy shedding light on a affiliate workflow, their cross -platform benefits ARSENAL for Windows, Linux and ESXI environment, as well as customizable encryption modes.
Analysis of the Windows and Linux Ransomware versions shows that it is very reminiscent of Inc Ransomware, indicating that the threat subjects have probably acquired the source code of the latter.
“Partners are stimulated with 80% of the revenue’s revenue, which reflects a competitive strategy that is managed by a set,” this – Note. “Lynx recently added several encryption modes:” fast “,” average “,” slow “and” whole “, giving partners the freedom of adjusting a compromise between the speed and depth of file encryption”.
“The sets in the group on the selection on underground forums emphasize the tough check process for petisters and qualified invasion, emphasizing the focus of Lynx on surgical safety and quality control. They also offer” colli -centrics “for persecution of victims and expanded storage solution Profit results ”.
In recent weeks, financial motivated attacks have also been observed Phorpiex (AKA TRIK) Batnet malicious software distributed via phishing -leaves to deliver Castle Ransomware.
“Unlike past incidents for Rushing LockBit, the actors threatened on the Phorpiex for delivery and execution of the Lockbit Redemption,” cyber noted In the analysis. “This technique is unique because the deployment of redemptions usually consists of human operators.”
Another significant initial vector of infection concerns the operation of unprotected VPN (eg Orthodox locker Ransomware.
The attacks are also characterized by the use of tunnel tools to maintain perseverance as well as using your own vulnerable driver (Byovd) Methods of disconnecting final points protection.
“After gaining environmental access and exploration, these tunnel tools are strategically deployed on critical network devices, including ESXI Hosts, Windows Hosts, VPN and Network Storage (NAS),” Sygnia researchers – Note.
“Signing on these devices, the attackers provide reliable and reliable communication channels to maintain access and orchestration of their malicious activities throughout the broken network.”
Landship Redemption – under the guidance Actors threaten new and old – continues to be able to flow, and attacks that are carried from traditional encryption to theft of data and extortion, even if the victims are increasingly refusing to pay, leading to a Reduced payments In 2024.
“Groups such as RansomHub and Akira now stimulate stolen data with great rewards, making these tactics quite profitable,” – cybersecurity – Note.