You come to the office, turn the system and panic sets. Each file is blocked and each system is frozen. Demand of the ransom on your screen is flashing: “Pay 2 million bitcoin for 48 hours or lose everything.”
And the worst thing is that even after payment, there is no guarantee that you will return your data. Many of the victims transfer money without getting anything in return, or worse, hit again.
This is not rare. The ransomware attacks are Summons Worldwide, from hospitals and banks to small companies. The only way to stop the damage is to actively analyze suspicious files and links before they can be executed.
Below we break up the top three ransomware in 2025: Lockbit, Lynx and Virlock, and learn how interactive analysis helps businesses discover and stop them until it is too late.
Castle: tease return in 2025
Lockbit is one of the most famous ransomware groups, known for its highly effective encryption, double extortion tactics and the ability to avoid traditional security measures. Working on the Ransomware-How’s Service (RAAS), it allows branches to distribute malicious software, which will lead to extensive attacks in various fields.
Latest attacks and activities:
- London drugs (May 2024): Lockbit aimed at Canadian retailers of London drugs, causing all its places across Canada. Hackers demanded $ 25 million by seizing the employees after the company refused to pay.
- University Hospital Center, Zagreb (June 2024): She thwarted Croatia’s largest hospital, forcing staff to return to manual operation, while the attackers claimed that they had been explicit medical documents.
- Evolve Bank & Trust (June 2024): Violated sensitive financial data, and hackers falsely claim that they have information about the federal reserve. The attack caused concern with the EVOLVE links with large Fintech firms.
Sample lock:
Let’s carefully look at the sample of the required software in any safe sandbox.
 |
| File icons change inside any. Run Sandbox |
Inside the interactive sandbox, we notice the first thing that stands out: file icons that change to Lockbit logo. This is a direct sign of the required program.
Discover the ransom tactics in real time and prevents expensive violations before they take place.
Then there is a note on the redemption inside the sandbox, which states that your files were stolen and encrypted. The message is clear: pay ransom or data will be published on Tor.
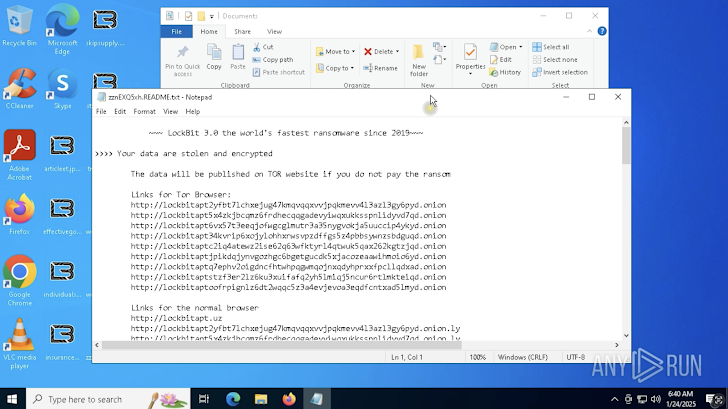 |
| A note on redemption is displayed in a safe setting |
On the right side of the screen, we see a detailed breakdown of each lock processes that are performed to attack the system.
 |
| Tree process demonstrates lock behavior |
By clicking on any process, security groups can analyze the exact tactics used in the attack.
 |
| Detailed rupture of processes inside the interactive sandbox |
This type of analysis is important for businesses, because it allows them to understand how the ransomware is distributed, determine weak points in their safety and take active measures to block similar threats before applying financial and surgical damage.
For a more in -depth analysis of the attack tactics, you can also click on the ATT & CK button in the upper right corner of the sandbox. This provides detailed information about each tactic, helping the team to clarify their protection and strengthen the response strategies.
 |
| MITER ATT & CK tactics and methods identified by any.Run |
In this case we see Lockbit using some dangerous methods:
- Having received higher privileges bypassing security control.
- Removal of saved data account from files and web browsers.
- Scan the system for collecting information before file encryption.
- Data encryption to block critical business operations.
New War on Attacking in 2025:
Despite the actions of law enforcement agencies, Lockbit continues to pose a significant threat to 2025. The alleged group leader, known as Lockbitsupp, warned about new ransom attacks that started in February this year. This means that businesses cannot afford to bring the guard.
Lynx: a growing threat to small and medium -sized businesses
Lynx is a relatively new ransom group that emerged in mid-2014 and quickly created a reputation for its very aggressive approach. Unlike large ransom gangs focusing on corporate giants, Lynx deliberately follows small and medium -sized enterprises throughout North America and Europe, using weaker safety measures.
Their strategy relies on double extortion. They do not just encrypt files, but also threaten the leakage of stolen data on both public sites and dark web forums when the victims refuse to pay. This makes the business up to the impossible choice: pay ransom or risks having confidential data, financial data and customer recording on the Internet.
Last attack Lynx:
In mid -January 2025, Velx Aimed at Lowe engineers, a well -known civil construction company based in Atlanta, Georgia. The attack has led to expressive sensitive data, including confidential information about the project and customer data. Given the firm’s involvement in critical infrastructure projects, this violation has caused considerable concern about the potential impact on federal and municipal contracts.
Sample Lynx:
Due to any interactive sandbox. We can analyze the complete Lynx Ransomware attack chain in a guided virtual setting without risking real systems.
View the Lynx Sandbox Analysis
At the moment we download and run the malicious executable file in any cloud sandbox. Redemption immediately begins to encrypt the files and changes their extension to .lynx.
 |
| Modification Files tab provides a change of file system activity |
A note will soon appear, and the desktop wallpaper is replaced for extortion, which directs the victims to the Tor site, where the attackers require payment.
 |
| Change the Lynx Ransomware Wallpaper, which is in any sandbox. |
Inside the sandbox Any.Run we can manually open the Readme.txt, dropped Lynx to view the reports of the buying exactly as the victim.
 |
| Note about ransom includes. |
In the Miter ATT & CK section, we get a precise gap of Lynx tactics and methods showing how it works:
 |
| MITER ATT & CK tactics and methods used by Lynx Ransomware |
- Encrypting files to block critical business data.
- Renaming the files to simulate other redemption deformations.
- Register request for scanning system details and safety software.
- Reading the processor information to evaluate the target environment.
- Checking software policy to determine security settings before starting.
VirLock: Self Rushing that does not die
Virlock is a unique strain that first appeared in 2014. Unlike the typical redemption, Virlock not only encrypts files, but also infects them, turning into a polymorphic infection. This dual ability allows you to spread rapidly, especially through platforms for storage and cooperation.
Latest attacks:
In recent Virlock analyzes, it is observed that the care is distributed through cloud storage and cooperation applications. When the user’s system is infected, Virlock encrypts and infects files that then synchronize with common clouded environments.
Employees who access these common files accidentally perform infected files, leading to further distribution to the organization.
Sample Virlock:
Let’s analyze the Virlock behavior using a real -time sample in the sandbox.
View the Virlock Sandbox Analysis
 |
| Virlock Ransomware Inside VM |
Just like LockBit and Lynx, Virlock lowers ransom when executed. However, this time it requires payment to Bitcoin, the total tactics among the operators.
In this particular Virlock sample asks for the equivalent of $ 250 in Bitcoin, threatening to constantly delete files if the ransom is not paid.
Interestingly, the ransom note does not only require payment. It also includes a Bitcoin guide that explains what it is and how victims can buy it for payment.
 |
| Ransom’s note requires to Bitcoin left Virlock |
While performing any.Run discovers some malicious activities showing how Virlock works:
 |
| Behavior of Virlock Ransomware, analyzed by interactive sandbox |
- A specific Virlock Mutex is detected, helping malicious software providing only one instance to avoid obstacles.
- Virrock performs commands through Batch files (.bat) by running cmd.exe to perform malicious action.
- Redemption changes the Windows registry via reg/regedit.exe will probably set stability or disabled security features.
Each sandbox session in any.Run automatically creates a detailed report that can be easily shared in the company. These reports are formatted for further analysis, helping to cooperate with security groups and developing effective strategies for extortion threats in 2025.
 |
| Created Report Up.Run Sandbox |
Redemption in 2025: an increasing threat you can stop
Redemption is more aggressive than if -no, violates enterprises, theft of data and requires millions of redemption. The cost of the attack includes lost operations, damaged reputation and stolen customer trust.
You can stop redemption before it fixes you. Analyzing suspicious files in any interactive sandbox.
Try any.Run free for 14 days To actively determine cyber -defeat to your business until it is too late!

