Startup artificial artificial intelligence of Chinese artificial intelligence (AI) DepthWhich in recent days has had a meteorite growth in popularity, left one of its databases that could allow malicious actors to access sensitive data.
The Clickhouse Database “Allow Database Controls, including the ability to access internal data,” Wiz Security Gal Nagli researcher – Note.
The exposition also includes more than a million lines of magazine streams containing chat history, secret keys, details and other very sensitive information, such as API secrets and operating metadata. Since then, Deepseek has connected the security hole after cloud -safety attempts to contact them.
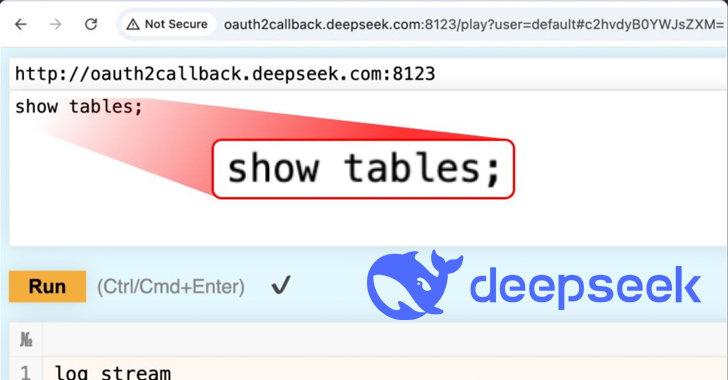
The database located on the oauth2callback.deepsek (.) Com: 9000 and Deepseek (.) Com: 9000, said, allowed unauthorized access to a wide range of information. The exposition, WIZ noted, allowed the database full control and the potential escalation of privileges in the Deepseek environment without requiring authenticity check.
This involved the use of the HTTP Clickhouse interface to perform arbitrary SQL requests directly through the web browser. It is currently unclear when other malicious subjects have taken the opportunity to access or download data.
“The rapid acceptance of AI services without proper security is risky,” Valgli said in a statement shared with Hacker News. “Although great attention around the safety of II is focused on futuristic threats, real dangers often come from major risks – as a random external database.”
“Customer data protection must remain a top priority for security teams, and it is very important that security groups work closely with AI engineers to protect data and prevent the exposition.”
Deepseek became the theme of Du Jour in AI wheels for its innovative source models, which claim that the AI leading systems such as Openai, as well as effective and cost effective. His reasoning model R1 was Saying hello Like “AI’s Sputnik moment”.
AI Chatbot from Upstart ran to the top of the Android and iOS app repositories in several markets, even when it has become the goal of “large -scale malicious attacks”, which pushed it to a temporary break.
Y en update Published on January 29, 2025, the company stated that it determined the issue and that it was working on the implementation of the fix.
At the same time, the company was also at the end Concern national security for the US.
In addition, Deepseek’s apps became unavoidable In Italy shortly after the country’s data protection regulator demanded information about the practice of data processing and where she received her learning data. It is unknown whether the application was concluded in response to the caretaker’s questions.
Bloomberg. Financial Timesand The Wall Street Journal Also report that both Openai and Microsoft are checking, whether the Openai (API) Deepseek Programming Interface is used without the permission to study your own models at Openai systems, an approach called as, mentioned as distillation.
“We know that groups B (China) are actively working on the use of techniques, including what is known as distillation to try to repeat the advanced AI AI models,” the Openai press -secretary detach The Guardian.