Threat actors are exploiting an unspecified zero-day vulnerability in Cambium Networks cnPilot routers to deploy a variant of the AISURU botnet called AIRASHI to conduct distributed denial of service (DDoS) attacks.
According to QiAnXin XLab, the attacks have loan funds security flaw since June 2024. Additional details of the flaws have been withheld to prevent further abuse.
Some of the other flaws armed with a distributed denial of service (DDoS) botnet include CVE-2013-3307, CVE-2016-20016, CVE-2017-5259, CVE-2018-14558, CVE-2020-25499, CVE-2020-8515, CVE-2022-3573, CVE-2022-40005, CVE-2022-44149, CVE-2023-28771as well as those affecting AVTECH IP cameras, LILIN video recorders and Shenzhen TVT devices.
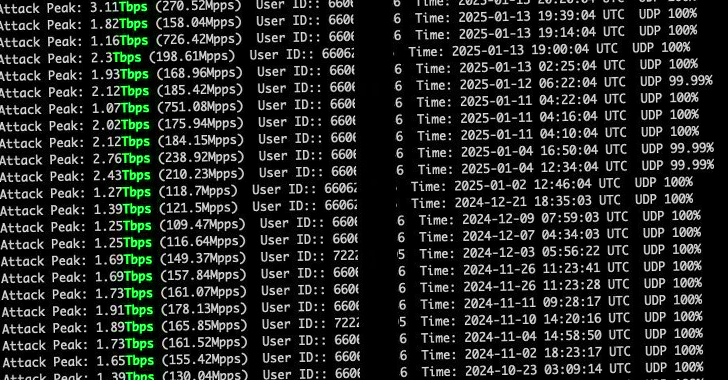
“The AIRASHI operator posted the test results of the DDoS attack on Telegram,” XLab said. “From historical data, it can be seen that the attack power of the AIRASHI botnet remains stable at around 1-3 Tbps.”
The majority of compromised devices are located in Brazil, Russia, Vietnam, and Indonesia, while China, the United States, Poland, and Russia are the main targets of the malware swarm.
AIRASHI is an option AYSURU (aka NAKOTNE) botnet that was previously flagged by a cybersecurity company in August 2024. due to a DDoS attack targeting Steam around the same time as the game’s launch Black Myth: Ukun.
A frequently updated botnet, individual AIRASHI variants have also been found to include proxy software functionality, indicating that threat actors intend to expand their services beyond facilitating DDoS attacks.
AISURU is said to have temporarily suspended its offensive activities in September 2024, only to re-emerge a month later with updated features (called “kitten”), and updated a second time in late November (aka AIRASHI).
“The kitten sample began circulating in early October 2024,” XLab noted. “Compared with previous AISURU samples, it simplified the network protocol. By the end of October, it had started using a SOCKS5 proxy to communicate with the C2 server.”
AIRASHI, on the other hand, comes in at least two different flavors –
- AIRASHI-DDoS (first discovered in late October), which mainly focuses on DDoS attacks, but also supports arbitrary command execution and reverse shell access
- AIRASHI-Proxy (first discovered in early December), which is a modified version of AIRASHI-DDoS with proxy functionality
The botnet, in addition to constantly tweaking its methods for obtaining C2 server details via DNS queries, relies on an entirely new network protocol that includes the HMAC-SHA256 and CHACHA20 algorithms for communication. Additionally, AIRASHI-DDoS supports 13 message types, while AIRASHI-Proxy supports only 5 message types.
The resulting data shows that attackers continue to use vulnerabilities in IoT devices both as an initial access vector and to create botnets that use them to add additional weight to powerful DDoS attacks.
The development comes as QiAnXin shed light on a cross-platform backdoor called alphatronBot that targets the Chinese government and businesses to trap infected Windows and Linux systems in a botnet. Since early 2023, the malware has targeted a legitimate peer-to-peer (P2P) open-source chat application called PeerChat talk to other infected nodes.
The decentralized nature of the P2P protocol means that an attacker can issue commands through any of the compromised nodes without having to route them through a single C2 server, making the botnet much more resistant to takedown.
“More than 700 P2P networks embedded in the backdoor consist of infected network device components from 80 countries and territories,” the company said in a statement. said. “Nodes include MikroTik routers, Hikvision cameras, VPS servers, DLink routers, CPE devices, etc.”
Last year, XLab also detailed a sophisticated and stealthy payload delivery framework, codenamed DarkCracks, that uses hacked GLPI and WordPress sites to operate C2 bootloaders and servers.
“Its main objectives are to collect sensitive information from infected devices, maintain long-term access, and use compromised, stable, and high-performance devices as relay nodes to control other devices or deliver malicious payloads, effectively hiding the attacker’s tracks,” the report said. said.
“Compromised systems were found to belong to critical infrastructure in various countries, including school websites, public transport systems and prison visitor systems.”