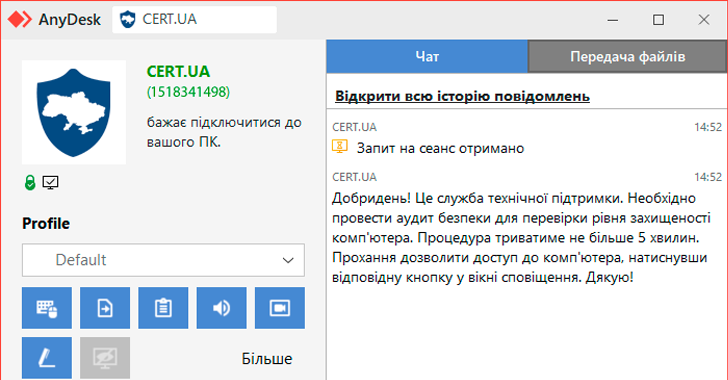
Ukraine’s Emergency Response Team (CERT-UA) warns of ongoing attempts by unknown threat actors to impersonate cybersecurity agencies by sending connection requests to AnyDesk.
AnyDesk’s requests claim they are intended to perform an audit to assess the “security level,” CERT-UA added, warning organizations to be wary of such social engineering attempts that seek to exploit user trust.
“It is important to note that CERT-UA may use remote access software such as AnyDesk under certain circumstances,” CERT-UA said. “But such actions are taken only after prior agreement with the owners of cyber defense facilities through officially approved communication channels.”
However, for this attack to succeed, the AnyDesk remote access software must be installed and running on the target’s computer. It also requires the attacker to own the target AnyDesk IDsuggesting that they may have to obtain the ID by other methods first.
To reduce the risk posed by these attacks, it is critical that remote access programs are enabled only for the duration of their use, and that remote access is coordinated through official communication channels.
News of the campaign comes after the State Service for Special Communications and Information Protection of Ukraine (SSSCIP) revealed that the cyber agency’s incident response center detected more than 1,042 incidents in 2024, with more than 75% of all events attributable to malicious code and invasion attempts.
“Cyber threat clusters were the most active in 2024 UAC-0010, UAC-0050and UAC-0006which specializes in cyber-espionage, financial theft and information-psychological operations,” SSSCIP. said.
UAC-0010, also known as Aqua Blizzard and Gamaredon, is believed to be the cause of 277 incidents. UAC-0050 and UAC-0006 were found to be associated with 99 and 174 incidents, respectively.
The development also follows the discovery of 24 previously unreported .shop top-level domains believed to be linked to the pro-Russian hacking group known as GhostWriter (aka TA445, UAC-0057 and UNC1151). connective scattered companies targeting Ukraine last year.
An analysis Security researcher Will Thomas ( @BushidoToken ) discovered that the domains used by these companies shared the same generic top-level domain (gTLD), registrar PublicDomainsRegistry, and Cloudflare name servers. All identified servers also have a robots.txt directory configured.
How Russian-Ukrainian war approaching the end of the third year, there were also cyber attacks recorded against Russia with a purpose steal sensitive data and disrupt business operations by deployment of ransomware.
Cyber security campaign FACCT last week attributed to in Sticky werewolf actor to a phishing campaign targeting Russian research and manufacturing companies to deliver a remote access Trojan known as Ozone, which is capable of providing remote access to infected Windows systems.
It also called Sticky Werewolf a pro-Ukrainian cyberespionage group that mainly deals with state institutions, research institutes and industrial enterprises in Russia. However, a preliminary analysis by Israeli cybersecurity company Morphisec found that the link “remains uncertain.”
It is not known how successful these attacks were. Some of the other threat groups that have been seen in recent months against Russian organizations include Core Werewolf, Venture Wolfand Paper werewolf (aka COFFEE), the latter of which used a malicious IIS module called Fallen to facilitate credential theft.