Cybersecurity researchers have discovered three security flaws in Planet Technology’s WGS-804HPT industrial switches that can be chained together to achieve remote code execution before authentication on sensitive devices.
“These switches are widely used in building and home automation systems for a variety of network applications,” Tomer Goldschmidt of Claroty said in a report on Thursday. “An attacker who can remotely control one of these devices can use them to further exploit devices on the internal network and perform lateral movement.”
The operational technology security firm, which conducted an extensive analysis of the firmware used in these switches using the QEMU framework, said the vulnerabilities lie in the dispatcher.cgi interface used to provide the web service. The list of disadvantages is given below –
- CVE-2024-52558 (CVSS Score: 5.3) – An integer restriction flaw that could allow an unauthenticated attacker to send a malformed HTTP request, resulting in a crash
- CVE-2024-52320 (CVSS Score: 9.8) – An operating system command injection flaw that could allow an unauthenticated attacker to send commands via a malicious HTTP request, leading to remote code execution
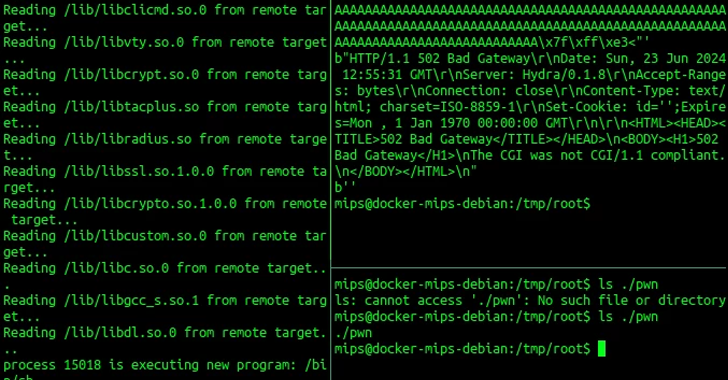
- CVE-2024-48871 (CVSS Score: 9.8) – Stack-based buffer overflow flaw that could allow an unauthenticated attacker to send a malicious HTTP request, leading to remote code execution
Successful exploitation of the flaws could allow an attacker to hijack the execution thread by injecting shellcode into an HTTP request and gain the ability to execute operating system commands.
After responsible disclosure, the Taiwanese company released patches for the flaws version 1.305b241111 released on November 15, 2024.