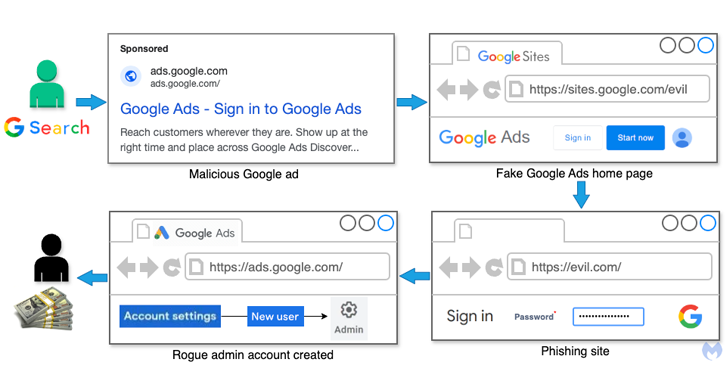
Cybersecurity researchers have warned of a new malicious ad campaign that targets individuals and businesses that advertise through Google Ads in an attempt to trick their credentials with fraudulent Google ads.
“The scheme is to steal as many advertiser accounts as possible by impersonating Google Ads and redirecting victims to fake login pages,” said Jerome Segura, senior director of threat intelligence at Malwarebytes. said in a report shared with The Hacker News.
It is believed that the ultimate goal of the campaign is to reuse the stolen credentials for further campaigns, as well as sell them to other criminals on underground forums. On the basis messages general on Reddit, Blueas well as Google support forumsthe threat has been in place since at least mid-November 2024.
An activity cluster is similar in many ways to companies that use hijacking malware to steal data associated with Facebook ads and business accounts in order to hijack them and use the accounts to dislodge malicious companies that further distribute the malware.
The newly identified company specifically targets users who search for Google Ads in Google’s own search engine to serve up false ads for Google Ads that, when clicked, redirect users to fraudulent sites hosted on Google Sites.
These sites then serve as landing pages that direct visitors to external phishing sites that are designed to capture their credentials and two-factor authentication (2FA) codes via WebSocket and transfer them to a remote server controlled by the attacker.
“False ads for Google Ads originate from a variety of individuals and businesses (including a regional airport) in a variety of locations,” Segura said. “Some of these accounts already had hundreds of other legitimate ads running.”
The genius aspect of the campaign is that it takes advantage of the fact that Google Ads does not require the final URL—the web page users are taken to when they click on the ad—must match the display URL as long as the domains match.
This allows threat actors to host their intermediate landing pages on sites.google(.)com while keeping their display URLs as ads.google(.)com. Moreover, the modus operandi involves the use of techniques such as fingerprinting, anti-bot traffic detection, CAPTCHA-based baiting, cloaking and obfuscation to hide the phishing infrastructure.
Malwarebytes said the collected credentials are then misused to log into the victim’s Google Ads account, add a new administrator, and use their budget to spend on fake Google ads.
In other words, threat actors hijack Google Ads accounts to promote their own ads and add new victims to the growing pool of compromised accounts used to further spread fraud.
“There appear to be several individuals or groups behind these companies,” Segura said. “Notably, most of them speak Portuguese and probably work from Brazil. The phishing infrastructure relies on intermediary domains with the .pt top-level domain (TLD), which indicates Portugal.”
“This malicious advertising activity is not infringing Google Advertising Policy. Threat actors are allowed to display fake URLs in their ads, making them look indistinguishable from legitimate sites. Google has not yet indicated that it is taking definitive steps to freeze such accounts until their security is restored.”
The discovery comes after Trend Micro discovered that attackers are using platforms like YouTube and SoundCloud to spread links to fake installers of pirated versions of popular software, which eventually lead to the deployment of various malware families, such as Amadey, Lumma Stealer, Mars Stealer, Penguish , PrivateLoader and Vidar Stealer.
“Threat entities often use reputable file hosting services such as Mediafire and Mega.nz to hide the origin of their malware and make detection and removal more difficult,” the company said in a statement. said. “Many malicious downloads are password-protected and encrypted, making analysis in security environments such as sandboxes more difficult and allowing malware to escape early detection.”