A serious security flaw has been discovered in ProjectDiscovery Nucleia widely distributed open source vulnerability scanner that, if successfully exploited, can allow attackers to bypass signature verification and potentially execute malicious code.
Tracked as CVE-2024-43405it has a CVSS score of 7.4 out of a maximum of 10.0. This affects all versions of Nuclei later than 3.0.0.
“The vulnerability results from a mismatch between the way the signature validation process and the YAML parser handle newline characters, combined with the way multiple signatures are handled,” it said. description vulnerabilities.
“This allows an attacker to inject malicious content into the template while preserving the valid signature for the benign portion of the template.”
Nuclei is a vulnerability scanner designed to scan modern applications, infrastructure, cloud platforms and networks for security flaws. The scanning mechanism uses templateswhich are nothing more than YAML files send specific requests to determine the presence of a defect.
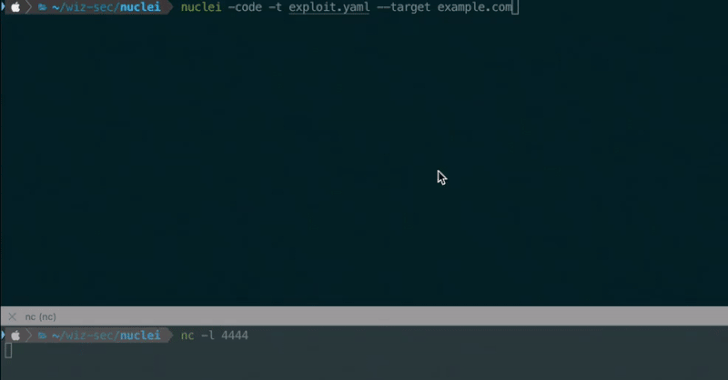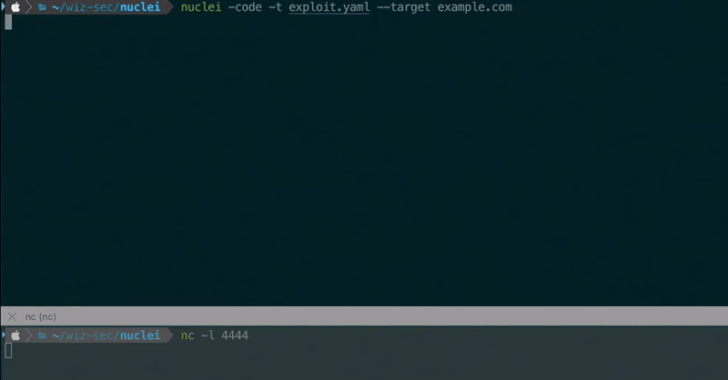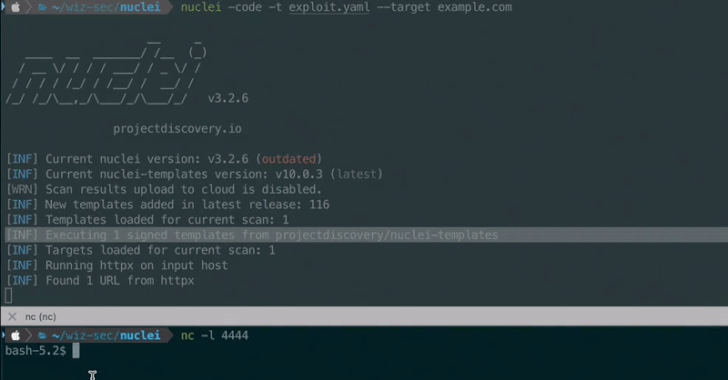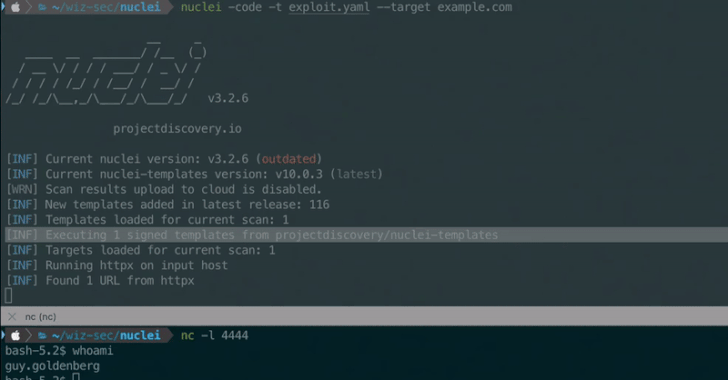
Additionally, it can enable external code execution on the host operating system by using the code protocolwhich gives researchers more flexibility in their security testing workflows.
Cloud security firm Wiz, which discovered CVE-2024-43405, said the vulnerability lies in the template signature validation process used to ensure the integrity of templates available in the official template repository.
Successful exploitation of the vulnerability bypasses this critical validation step, allowing attackers to create malicious templates that can execute arbitrary code and access sensitive data from the host.
“Since this signature verification is currently the only method available to verify Nuclei templates, it represents a potential single point of failure,” Wiz researcher Guy Goldenberg said in Friday’s analysis.
Essentially, the issue is due to the use of regular expressions (aka regex) to validate the signature and the parsing conflict that results from using both regular expressions and the YAML parser, which opens the door to a scenario where an attacker could type ” \r” such that it bypasses regular expression-based signature validation and is interpreted by the YAML parser as a line break.
In other words, these parse mismatches can be chained together to create a Nuclei pattern that uses “\r” to include a second “# digest:” line that evades the signature verification process but is parsed and executed by the YAML interpreter.
“Go’s regular expression-based signature validation treats \\r as part of a single line, while the YAML parser interprets it as a line break. This mismatch allows attackers to inject content that bypasses validation but is executed by the YAML parser,” explained Goldenberg. .
“The validation logic checks only the first # digest: line. Additional # digest: lines are ignored during validation, but remain in the content for YAML parsing and execution.”
Additionally, the validation process includes the step of excluding the signature row from the template content, but does so in such a way that only the first row is validated, thus leaving subsequent rows unvalidated but executable.
After responsible disclosure, it was reviewed by ProjectDiscovery on September 4, 2024. with version 3.3.2. The current version of Nuclei is 3.3.7.
“Aggresives can create malicious patterns containing manipulated digest # lines or carefully placed \r line breaks to bypass Nuclei’s signature verification,” Goldenberg said.
“The attack vector for this vulnerability occurs when organizations run untrusted or community-generated templates without proper validation or isolation. An attacker could use this functionality to inject malicious patterns that lead to arbitrary command execution, data theft, or system compromise.”