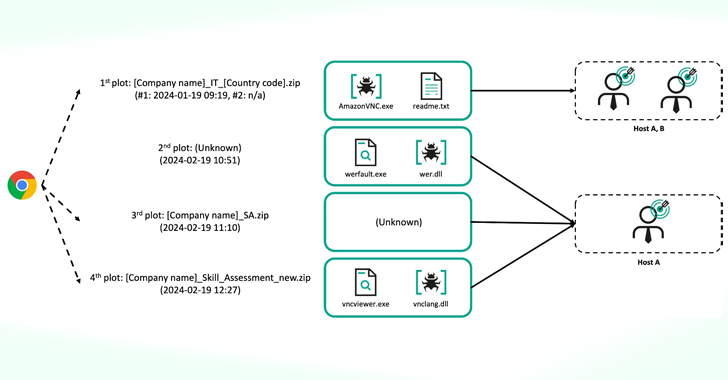
The Lazarus Group, a notorious threat linked to the Democratic People’s Republic of Korea (DPRK), was seen using a “sophisticated infection chain” to target at least two employees of an unnamed nuclear-related organization over a one-month period in January 2024
The attacks culminated in the deployment of a new modular backdoor called CookiePlusare part of a long-running cyberespionage campaign known as Operation Dream Job, which is also being tracked as NukeSped by the cyber security company Kaspersky. He has been known to be active since at least 2020, when he was exposed by ClearSky.
This activity often involves targeting developers and employees at various companies, including defense, aerospace, cryptocurrency and other global industries, with lucrative job opportunities that ultimately lead to the deployment of malware on their machines.
“Lazarus is interested in launching supply chain attacks as part of the DeathNote campaign, but this is mainly limited to two methods: the first is to send a malicious document or Trojan PDF viewer that displays individual job descriptions to the target,” Russian firm said in a comprehensive analysis.
“Secondly, by spreading trojanized remote access tools such as VNC or Putty to convince targets to connect to a specific server for a skill assessment.”
The latest series of attacks documented by Kaspersky involves a second method where an adversary uses a completely updated infection chain, delivering a trojanized VNC utility under the guise of conducting a skills assessment for IT positions at prominent aerospace and defense companies.
It should be noted that the Lazarus group’s use of fake versions of VNC applications for nuclear engineers was highlighted earlier by the company in October 2023 in the Q3 2023 APT Trends Report.
“Lazarus delivered the first archive file to at least two people in the same organization (we’ll call them Host A and Host B),” said researchers Vasyl Berdnikov and Sojun Ryu. “A month later, they tried to attack the first target more intensively.”
The VNC applications, a trojanized version of TightVNC called “AmazonVNC.exe”, are believed to have been distributed as both ISO images and ZIP files. In other cases, a legitimate version of UltraVNC was used to sideload a malicious DLL packaged in a ZIP archive.
The DLL (“vnclang.dll”) serves as the loader for the duplicate backdoor I LOST A PENwhich was discovered by Google-owned Mandiant in September 2024. It tracks a cluster of activity under the alias UNC2970. MISTPEN was found to be delivering two additional code-named payloads RollMid and a new variant of LPEClient.
Kaspersky said it also observed the CookieTime malware being deployed on Host A, although the exact method used to do so remains unknown. The first revealed by the company in September and November 2020, CookieTime is so named for using encoded cookie values in HTTP requests to receive instructions from the command and control (C2) server.
Further investigation of the attack chain revealed that the threat actor moved laterally from Host A to another machine (Host C) where CookieTime was again used to dump various payloads between February and June 2024, such as:
- LPEClient, a malware that comes with profiling capabilities for compromised hosts
- ServiceChanger, a malware that terminates a target legitimate service in order to load a fake DLL embedded into it using an executable via DLL sideloading
- Charamel Loader, a malicious loader that decrypts and loads internal resources such as CookieTime, CookiePlus and Forest Tiger
- CookiePlus, a new plugin-based malware that loads both ServiceChanger and Charamel Loader
“The difference between each CookiePlus loaded by the Charamel Loader and the ServiceChanger is the way it is executed. The former runs as a single DLL and contains C2 information in its resource section,” the researchers noted.
“The latter gets what is stored in a separate external file like msado.inc, which means CookiePlus has the ability to get the C2 list from both an internal resource and an external file. Otherwise, the behavior is the same.”
CookiePlus got its name from being disguised as an open source Notepad++ plugin called ComparePlus when it was first found in the wild. The attacks targeting the nuclear organization were found to be based on another named project DirectX wrappers.
The malware acts as a bootloader to retrieve a Base64 and RSA encoded payload from the C2 server, which is then decoded and decrypted to execute three different shellcodes or DLLs. Shellcodes are equipped with functions to gather system information and put the main CookiePlus module to sleep for a certain number of minutes.
CookiePlus is suspected to be a successor to MISTPEN due to similarities in the behavior of the two malware families, including the aspect that both disguised themselves as Notepad++ plugins.
“Throughout its history, the Lazarus group has used only a small number of modular malware frameworks, such as Eye and Gopuram Loader“, Kaspersky said. “The fact that they do introduce new modular malware like CookiePlus shows that the group is constantly working to improve its arsenal and infection chains to avoid detection by security products.”
The findings come after blockchain firm Chainalysis revealed that North Korea-linked threat actors stole $1.34 billion in 47 cryptocurrency breaches in 2024, up from $660.50 million dollars in 2023. This included the hack of Japanese cryptocurrency exchange DMM Bitcoin in May 2024, which was affected. a loss of $305 million at the time.
“Unfortunately, it seems that North Korea’s crypto attacks are becoming more frequent,” the company said in a statement said. “Notably, attacks costing between $50 million and $100 million and over $100 million occurred significantly more frequently in 2024 than in 2023, suggesting that North Korea is getting better and faster at mass exploits.”