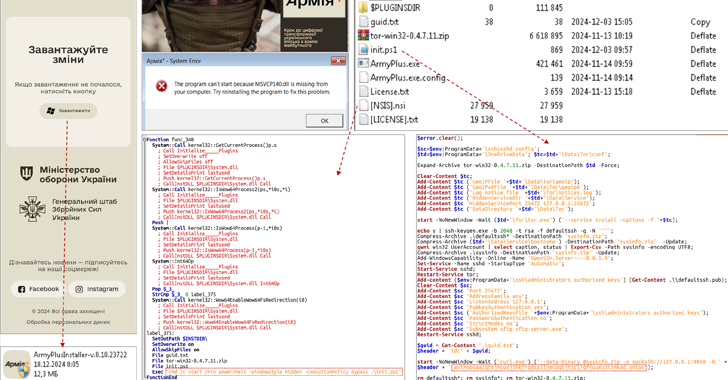
The Computer Emergency Response Team of Ukraine (CERT-UA) has opened that a threat actor it tracks as UAC-0125 is using the Cloudflare Workers service to force military personnel in the country to download malware under the guise of Army+a mobile application that was introduced by the Ministry of Defense back in August 2024 to make the armed forces paperless.
Users visiting the fake Cloudflare Workers websites are prompted to download the Army+ for Windows executable file created using the Nullsoft Scriptable installer (NSIS), an open source tool used to create operating system installers.
Opening the binary displays a decoy file to run and executes a PowerShell script designed to install OpenSSH on the infected host, generate an RSA cryptographic key pair, add the public key to the “authorized_keys” file, and transmit the private key to the monitored server attacker, using the anonymous TOR network.
The ultimate goal of the attack is to allow an adversary to gain remote access to the victim’s machine, according to CERT-UA. It is currently unknown how these links are distributed.
The agency further noted that UAC-0125 is associated with another cluster named UAC-0002which is better known as APT44, FROZENBARENTS, Sandworm, Seashell Blizzard and Voodoo Bear, is an Advanced Persistent Threat (APT) group associated with Unit 74455 of the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU).
Earlier this month, Fortra revealed he noticed a “growing trend in legitimate abuse of services” where attackers are using Cloudflare Workers and Pages to host fake Microsoft 365 login pages and human verification to steal user credentials.
The company said it has seen a 198% increase in phishing attacks on Cloudflare pages, increasing from 460 incidents in 2023 to 1,370 incidents as of mid-October 2024. Likewise, the number of phishing attacks using Cloudflare Workers increased by 104%, increasing from 2,447 incidents. in 2023 to 4,999 incidents to date.
Development occurs as the European Council imposed sanctions against 16 individuals and three organizations responsible for “destabilizing actions of Russia abroad”.
This includes Military unit 29155 GRUfor involvement in foreign assassinations, bombings and cyber attacks across Europe, Groupe Panafricain pour le Commerce et l’Investissement, a disinformation network that conducts pro-Russian covert influence operations in the Central African Republic and Burkina Faso, and African Initiative, a news agency that expanded Russian propaganda and disinformation in Africa.
Sanctions are also targeted Doublea Russian-run disinformation network known for spreading narratives and supporting Russia’s war of aggression against Ukraine, manipulating public opinion against the country, and eroding support for the West.
For this purpose, Sofia Zakharova, the head of the Department of the Presidential Affairs Department of the Russian Federation for the development of information and communication technologies and communication infrastructure, and Mikala Tupikin, the head and founder of Structura Group (also known as Company Group Structura), had their assets frozen and were banned from traveling.
Tupikin was also there sanctioned by the US Treasury’s Office of Foreign Assets Control (OFAC) back in March 2024 for involvement in foreign influence peddling.